Until recently, most people didn't have to worry about the word ‘encryption’. In fact, many businesses didn't either. Cyber attacks and public conflicts are now common in the news – such as between the FBI and Apple and then government officials targeting Facebook. Everyone is suddenly becoming more aware of encryption and its importance.
We are all now more aware of the need to protect our sensitive data, both at work and at home, but people often feel unsure of how to do so. What does encryption actually mean? How should you encrypt your data? And which tools can you use?
Read this guide to find out the main points about encryption and 10 steps to get started.
What Is Data Encryption?
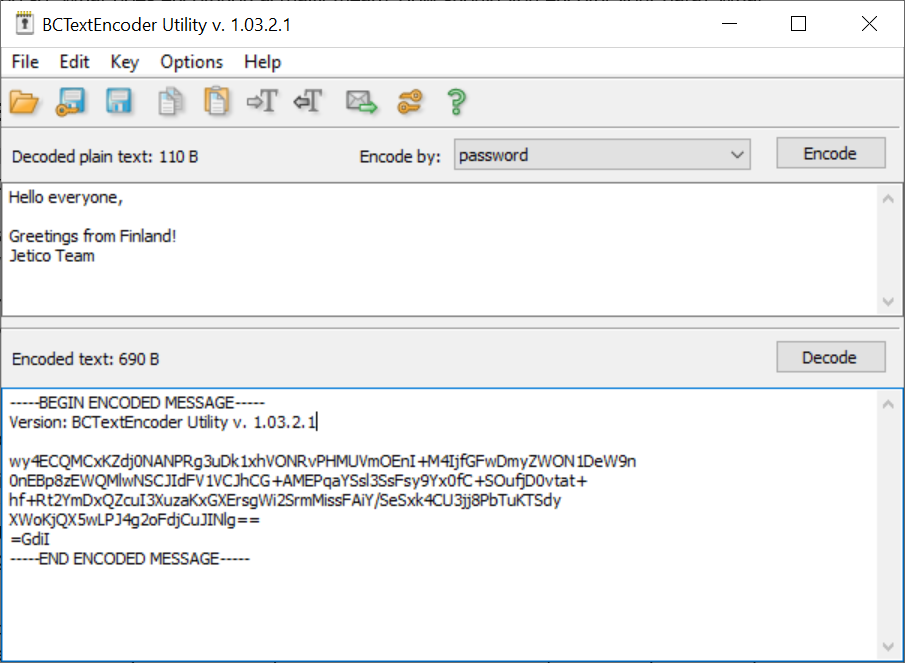
Data encryption is the act of transforming your data into random characters that cannot be read without the correct key. It looks something like this:
To scramble and unscramble the text, modern encryption makes use of sophisticated algorithms and different keys. Let me tell you more…
What Is an Encryption Algorithm?
An encryption algorithm is the process that encrypts and decrypts your data. Popular algorithms at present include AES, RC-6 (REA), and Twofish. Different algorithms work in slightly different ways. These algorithms vary in strength to some degree, but there’s not a significant difference.
Which algorithm is best for you depends on your needs, the type of data and your infrastructure. In most cases, anything is fine; if you have more concerns, you can discuss your situation with a cyber security specialist.
What Is an Encryption Key?
An encryption key is the specific code that translates your encrypted data into readable data, and vice versa. Encryption keys differ depending on the types of encryption algorithms they are used for:
- Symmetric
With this algorithm, you use only one key for both encrypting and decrypting. An example is password-based encryption. You send the password (separately) to the person you are sending the file; and then they use the password to unlock the file. This system tends to be faster, but does rely on the key being kept safe; if a bad guy finds the key then the scheme becomes useless.
- Asymmetric
This algorithm uses a pair of keys. A public key is used to encrypt the data, and a private key to decrypt. Your public key is just that – public. You can make it widely available because a public key can't be used to decrypt anything, which allows others – vendors, clients, anyone – to send you encrypted files. The private key is not at risk of being intercepted in transit.
What Is Encryption Key Size?
Encryption keys can vary in size. The larger the key size, the harder it is to break by using so-called brute force attacks (when a computer simply runs through every possible combination until it hits the right one). The number of combinations is higher.
Most modern algorithms start at 128-bit keys, which have 340 trillion possible combinations. Although there are larger keys (256-bit), it would take current computers longer than the age of the universe to brute force a 128-bit key!
What Data Can You Encrypt?
All of it. You can easily encrypt all your data. Data is generally in one of three states:
- At rest – meaning stored in a digital form in a specific place. Data at rest is the data on your hard drive, the photos on your smartphone, the backup you keep on a USB stick, etc.
- In transit – meaning in the process of being transferred from one place to another. Data in transit includes email, instant messages and data being uploaded to or downloaded from cloud storage.
- In use – meaning actively being read and changed. Data in use is the data in your computer's active memory (RAM), cache, etc.
10 Steps to Get Started on Encrypting and Protecting Everything
So how will you implement encryption? Well if possible, encrypt everything. This list is at least a great starting point.
- Home Network
While some people still use wires to connect computers, your home or office network likely runs primarily on Wi-Fi. Wi-Fi routers support wireless encryption, which requires a password to connect to the network. Check the manual on your router for how to make sure encryption is enabled. Some ISPs now ship routers with encryption pre-enabled. For added security, remember to change the default access password. And make sure your router firmware is updated, so you aren't using WEP – for which every hacker now has the key.
- Internet Traffic
Avoid websites if the address does not start with https – the added ‘s’ is for secure. Even Google is now penalizing websites only with unsecure http. Be sure to double check before sending sensitive information. HTTPS Everywhere is an extension for Firefox, Chrome, and Opera which makes all websites into https. Also worth considering a VPN, which will encrypt all your traffic data. Best to avoid free VPNs, as they are likely less trustworthy about what they do with your ‘protected’ data. If you ever use public Wi-Fi, then you need reliable VPN software.
- Computer
Using whole disk encryption is the best and easiest way to protect your files. This is common for organizations that handle sensitive information, such as health records.
- External Hard Drive
Many people easily remember to encrypt their computer; meanwhile they might forget about their external hard drives. If you're the only person using the drive, then just use whole disk encryption. Otherwise, encrypt the sensitive files and folders and leave shared information visible.
- Communications
Think basic text messages are secure? They aren't. You can install an encrypted messaging app to protect them. These apps typically also encrypt video and voice calls.
- Email
After your hard drives, your email is the most important thing to encrypt. Email can be one of the least secure methods of communication. Would you write personal information on a postcard and then mail it? Email encryption is generally done using asymmetric encryption. Make sure to encrypt all your email.
- Files and Folders
Whole disk encryption is good, but some people find it easier to just encrypt certain files and folders as needed.
- Cloud
If you store cloud backups, make sure they are encrypted too. Again, people often forget to encrypt their backups. While some shared files might need to be in the clear, most of your cloud data should be encrypted.
- Phone
Most modern smartphones now come with decent encryption built in. For better security, consider adding a tool from an encryption company.
- Passwords
Finally, don't forget about your passwords. Forget about sticky notes and start storing your passwords securely.
Hopefully you learned some basics on how to start encrypting and protecting all your data. It's easier than you might think. And once you’re in the habit of encrypting, you won’t even notice those little extra steps you take to keep your data safe.
Happy Encrypting!
Related Articles
Commercial or Open-Source Encryption Software – Whose Side Are You On?
Guide to Enterprise Data Encryption and Protection Solutions
The Guide to Encrypting Data in the Cloud