BestCrypt Data Shelter
Data in Use Protection to Lock Down Active Files from Ransomware & Cyber Threats
Protect selected folders from unauthorized access – including ransomware
Create & apply flexible protection policies for multiple folders
Detect & automatically block suspicious or untrusted processes

New Version Out Now!
Smarter Policies. Simpler Experience. Same Trusted Security.
Protect Sensitive Data in Use with BestCrypt Data Shelter
Did you know that data is more vulnerable when it’s in use?
Data in use is accessible and typically exists in an unencrypted state, which makes it vulnerable to ransomware, malware and prying eyes. BestCrypt Data Shelter by Jetico provides robust “data-in-use protection” by keeping your sensitive files secure even while they are being accessed or edited. With BestCrypt Data Shelter, you can proactively defend against ransomware attacks by blocking unauthorized applications from accessing your protected folders, safeguarding your data without compromising usability. Jetico’s free tool can also help protect against threats like AI-powered scams that rely on unauthorized access to sensitive information.
While BestCrypt Data Shelter is free for personal use, please get in touch with us for enterprise licensing and support.
Proven Ransomware Protection – Tested with KnowBe4’s RanSim
To verify BestCrypt Data Shelter’s protection capabilities against cyber threats, we ran KnowBe4’s RanSim, a widely recognized ransomware simulator that tests various attack scenarios in a controlled environment.
What Is RanSim?
RanSim is a free tool by KnowBe4 that mimics real ransomware behavior to test how well a system can defend itself. It simulates 23 known ransomware attacks, from file encryption to stealthy deletion.
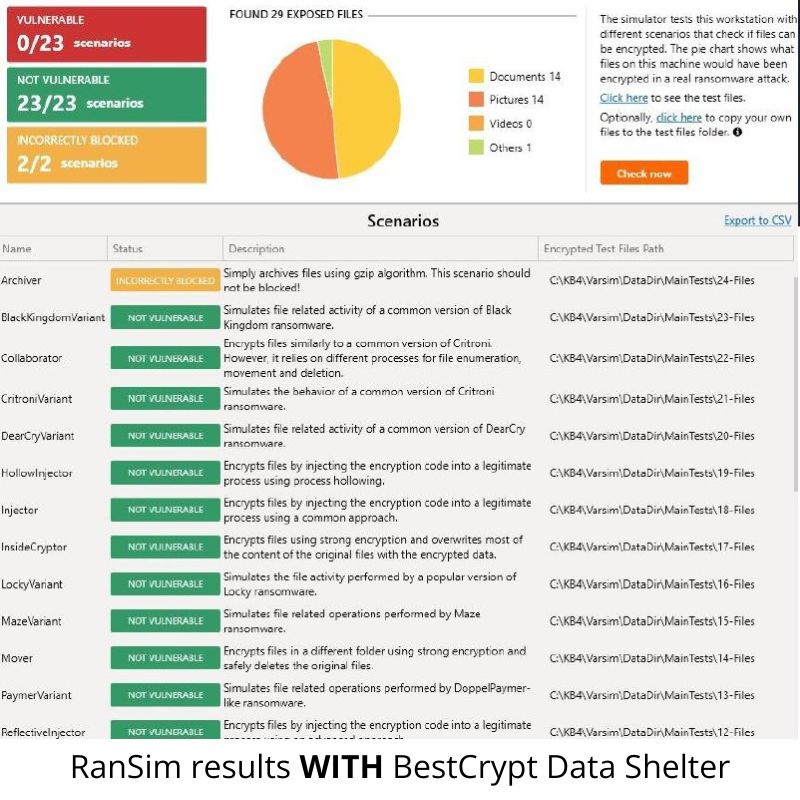
0 Vulnerabilities Detected with BestCrypt
BestCrypt Data Shelter effectively blocked all simulated ransomware activity. No unauthorized access to protected folders occurred during any of the 23 test scenarios run by KnowBe4’s RanSim tool. All 23 attack simulations were neutralized, with protected folders remaining fully secure throughout the test.
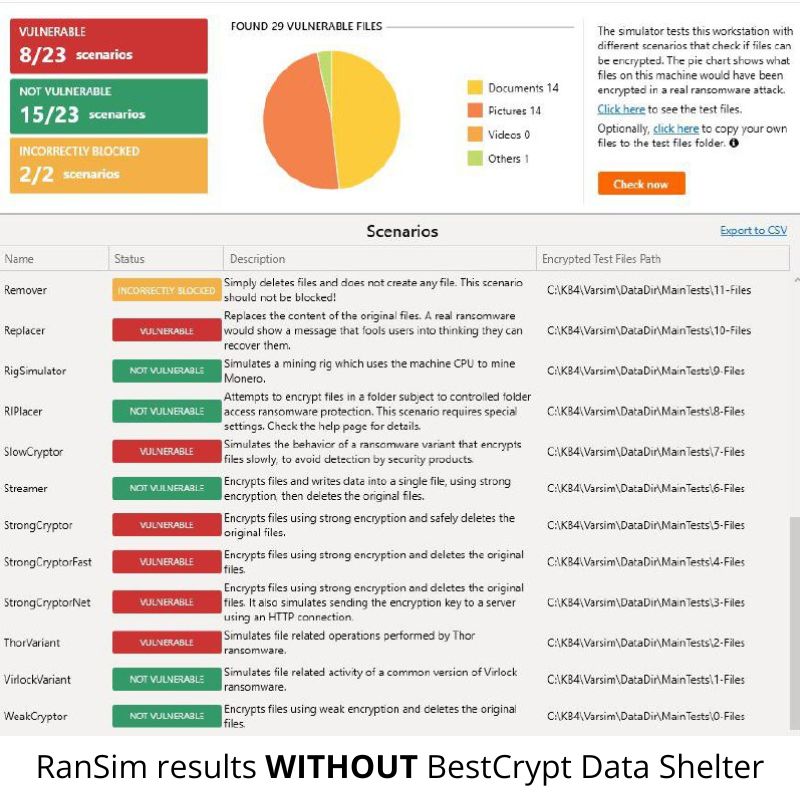
Before Enabling BestCrypt Data Shelter:
❌ 8 out of 23 ransomware simulations were successful
After Enabling BestCrypt Data Shelter:
✅ 0 out of 23 simulations were successful
Why Use BestCrypt Data Shelter?
Protecting sensitive files during active use is essential to ensuring data security. Here’s how BestCrypt Data Shelter helps keep your data safe without interrupting your workflow:
- Real-Time Data-in-Use Protection from Ransomware & Cyber Threats – Ensure that sensitive files remain secure during active use. BestCrypt Data Shelter automatically protects designated folders and files from unauthorized programs, including ransomware, as they’re accessed, edited or in active use, keeping your data safe in real-time.
- Block Unauthorized Access – Limit access to essential files by automatically blocking unauthorized applications or users, ensuring that only trusted programs and personnel can interact with sensitive data.
- Flexible Security with Smart, User-Friendly Controls – Easily designate folders and file types for protection with fully customizable settings. The latest version of BestCrypt Data Shelter includes a new intuitive UI and smart suggestions based on your folder access patterns, simplifying setup and management.
How to Get Started with BestCrypt Data Shelter
BestCrypt Data Shelter provides data-in-use protection, effectively safeguarding sensitive files from unauthorized processes and users. By distinguishing between trusted, uninfected processes and those compromised by malware, BestCrypt Data Shelter blocks malicious attempts to access your protected folders.
Watch our quick 3-step video to get started with BestCrypt Data Shelter, or follow these simple steps:
- Download & Install
Install BestCrypt Data Shelter on your Windows computer. - Select Protected Folders & Customize Security Settings
Open the program and specify which folders or file types you want to secure. Set permissions, such as access levels and trusted applications, to fit your security needs. - Activate Protection
Start BestCrypt Data Shelter to enable real-time protection for your selected files.
BestCrypt Data Shelter makes it simple to secure data in use, giving you confidence that your sensitive files are safeguarded whenever they’re accessed.
Download BestCrypt Data Shelter for Free
Enjoy data-in-use protection to secure active files instantly!
News & Blogs
Stay updated with the latest news, insights, trends and expert tips on data protection and cybersecurity.
Check back here regularly for news and blogs