



The IEEE 2883-2022 standard was issued by the Institute of Electrical and Electronics Engineers in August 2022. Providing guidelines for sanitizing logical and physical storage, as well as technology-specific requirements for eliminating recorded data, the IEEE 2882-2022 aims to counter emerging challenges to data storage brought about by new technology.
In this blog, you can find an overview of IEEE 2883-2022 and why it’s important to your organization. You will also learn about the data erasure methods and techniques outlined in the standard, as well as the importance of verifying your sanitization results.
Media sanitization is the process of erasing information from a storage device in a way that ensures it cannot be retrieved by third parties. After effectively sanitizing a device, the removed data should be unrecoverable even with the use of advanced forensic tools. In addition to removing the files and folders from your storage device, the sanitization process will securely remove all Data Remanence.
Despite the latest revision coming in 2014, the most commonly used data erasure standard today is still the NIST SP 800-88 Guidelines for Media Sanitization. The changes that have come about to data storage technology in the last 10 years, however, require updated standards to account for devices that are now commonly used in the workplace and at home. That’s precisely what the IEEE 2882-2022 Standard for Sanitizing Storage does, with the publication offering guidance on how to sanitize NVMe, SATA, SCSI and other types of modern drives.
The IEEE 2883-2022 Standard for Sanitizing Storage describes 3 methods that can be used for erasing physical storage: Clear, Purge and Destroy.
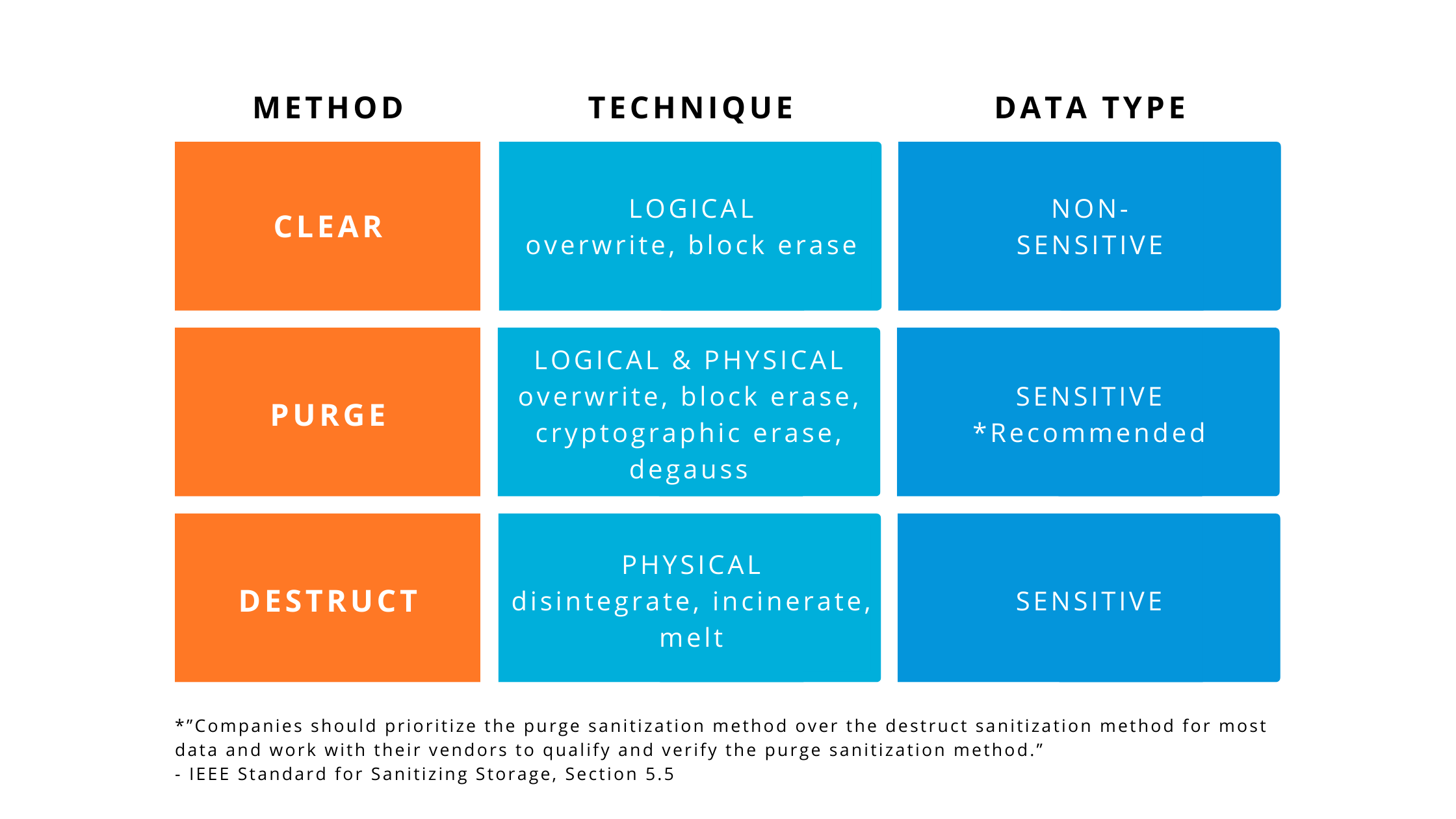
After using one of the above sanitization methods to remove data from your device, you should finalize the process by verifying your results. Verification is an important step that checks all data has been removed, therefore delivering extra confidentiality.
Depending on the sanitization technique used, the verification process will differ:
BCWipe Total WipeOut is a long-trusted data wiping solution that securely erases hard drives beyond forensic recovery. If you plan on following the IEEE 2883-2022 standard to purge data, BCWipe Total WipeOut simplifies the process by allowing you to add a verification step to the end of sanitization operations by doing nothing more than ticking a checkbox.
Get started with Jetico’s secure data sanitization solution by signing up for your free trial of BCWipe Total WipeOut or contacting out data protection specialist for a free consultation.
Related Articles
Data Sanitization 5 Common Myths
Hardware Decommissioning Process: A 5-Step Checklist
NIST SP 800-88 Guidelines for Media Sanitization Explained
DoD 5220.22-M Explained - Data Erasure Standards
CMMC 2.0 Levels, Controls & Framework for Media Sanitization Requirements
How to Securely Wipe Your Windows 11 Computer Clean
How to Wipe an NVMe Drive
How to Obtain a Certificate of Destruction

Hannaleena Pojanluoma has been leading Jetico as CEO since May 2023, bringing with her more than 20 years of sales, marketing and technology experience. Previously working for a range of international companies in her native Finland, Pojanluoma has a broad understanding of diverse international markets.
Pojanluoma has been essential in driving sales growth since joining Jetico in October 2015. Her efforts have been concentrated on boosting sales and brand awareness in key European countries such as the United Kingdom, Germany and Italy.
As a member of Jetico's Board of Directors, she joins influential figures such as Tommi Rasila and Umeshchandra Gowda.
