
Features - BestCrypt Volume Encryption
Encrypt System & Boot Volumes 

Encrypts the volume from which operating system (OS) boots from, as well as the volume where OS stores system files. Check out the 5 benefits of using volume encryption vs. disk encryption.
Pre-Boot Authentication 

User authentication before operating system loads is required when OS System/Boot volume is encrypted.
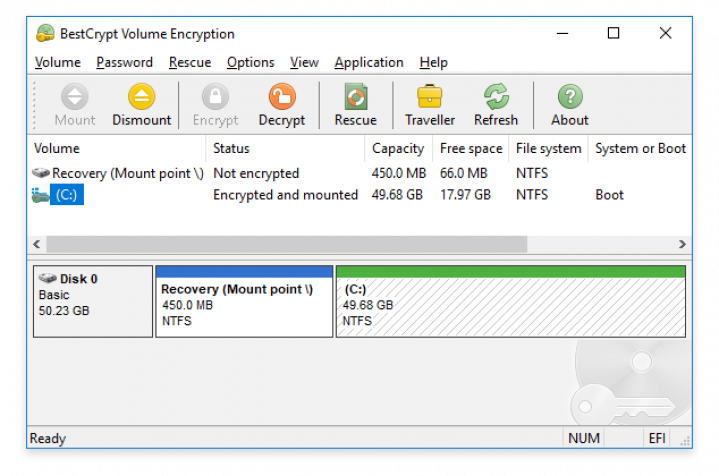
Strong Encryption Algorithms 

BestCrypt Volume Encryption utilizes strong encryption algorithms (AES, ARIA, Camellia, Serpent and Twofish). Every algorithm is implemented with the largest possible key size defined in the algorithm's specification, all available with the most secure XTS encryption mode (learn more).
Two-Factor Authentication 
Two-Factor Authentication (2FA), aka Multi-Factor Authentication (MFA), is an extra layer of security added to password protection. BestCrypt Volume Encryption supports Yubikey and SafeNet eToken hardware tokens, as well as regular removable disks, for secure hardware storage of encryption keys.
Self-Efficient Encrypted USB 
Create encrypted removable drives that can be later accessed with your password from another computer where BestCrypt Volume Encryption is not necessarily installed.
Scalable Disk Encryption 
Choose to encrypt entire computer, selected disk volumes or a single volume - whether entirely, or just the disk space taken by files.
Single Sign-On 
Save time by automatically logging in to Windows with your encryption password.
Secure Hibernation 
To protect your computer when left unattended BestCrypt Volume Encryption automatically locks it during hibernation, encrypts contents of the hibernation file and requires authentication on wake-up.
Support for UEFI Secure Boot 
Protects your password and encryption keys from being intercepted (e.g. with an Evil Made Attack) by checking digital signature of all modules responsible for booting encrypted computer.
Support for Trusted Computing (TPM) 
Configure Unattended Mount at Restart to store encryption keys securely inside a Trusted Platform Module allowing to reboot without authentication. Useful for updating encrypted servers, remote management or sending encrypted computers to a service.
Transparent Operation 

BestCrypt Volume Encryption does not interrupt with your workflow. You can continue using your computer while encryption is in progress. You can also pause the encryption process and resume it later.
Rescue Functions to Decrypt Volumes in Emergency Case 

- Bootable CD/DVD
- Bootable USB
- Rescue decryption of non-system volumes with Rescue File
- Windows bootable Live CD
* New Features in Version 5 for Windows *
Added Resilience against Cyberattacks & Enhanced Security
- Protection from brute-force attacks — Customize parameters of Scrypt key derivation algorithm for extra security against password-iterating attacks.
- Manage self-encrypting drives — Enable whole disk encryption on TCG Opal 2.0 storage drives for an extra layer of protection.
- Two-factor authentication — Boost your security with 2FA for a range of new hardware, including PKCS #15-compliant smart cards and crypto tokens.
Improved Performance
- Faster encryption with added hardware-level acceleration for ARIA and Camellia encryption algorithms.
- Seamless, on-the-fly encryption with AES implementations optimized for x64 CPU architecture.
- Performance upgrade for the fastest NVM Express storage devices.
Better Usability
- Customizable graphic themes, international language support and virtual keyboard added to UEFI pre-boot environment
- BestCrypt Volume Encryption modules now integrated with Windows Recovery Environment (WinRE), allowing for smooth troubleshooting in Windows without removing encryption.
- International characters now available for encryption passwords, increasing potential character variety and making password attacks more difficult.
More References
BestCrypt Volume Encryption Documentation and Release Notes
Encrypt Selected Files and Folders (BestCrypt Container Encryption)
Wipe Selected Files & Folders Beyond Forensic Recovery (Endpoint Data Protection)
Deploy, Monitor, Set Encryption Policy Distribution & Password Recovery with Jetico Central Manager (Enterprise Edition)

English
Alternative languages (only for Windows)
Jetico is only responsible for the English language version. Yet many of our users have kindly contributed translations of the software so it appears in their native language. Jetico appreciates our open global community of dedicated users and enables the distribution of these user-contributed translations:
Arabic
Chinese
Czech
Danish
Dutch
Farsi
German
Italian
Japanese
Polish
Russian
Serbian
Spanish
If you would like to translate BestCrypt Volume Encryption client software into your native language, contact Jetico Technical Support.

Windows Users
Windows 11
Windows 10
Windows 8
Windows 7 SP1
Windows Vista (x86)*
Windows XP (x86)*
Windows Server 2019
Windows Server 2016
Windows Server 2012
Windows Server 2011
Windows Server 2008 R2
Windows Server 2003 (x86)*
(32- and 64-bit versions, unless stated otherwise)
*For legacy OS including Windows XP (x64), Windows Vista (x64), Windows Server 2003 (x64) and Windows Server 2008 (x64), use this version: BestCrypt Volume Encryption for legacy OS

Mac Users
macOS X 10.9 and later







