System tray icon
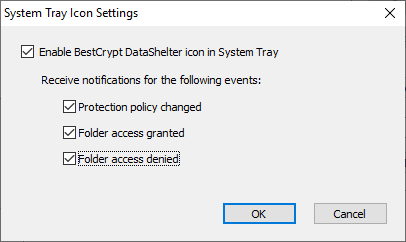
BestCrypt DataShelter can display its System Tray Icon in the right bottom corner of the desktop. To activate the icon, click the More... button in the main window of the program and run the System tray icon command in the appeared menu. The following dialog window will appear.
|
|
|
|
BestCrypt DataShelter icon in the System Tray will appear if you set the Enable BestCrypt DataShelter icon in System Tray option in the dialog window and click the Ok button. Please note that BestCrypt DataShelter shows notification messages in the System Tray area. By setting options for the various events reported by the program you can increase or decrease the number of the reported events.
If you click the BestCrypt DataShelter Icon in the System Tray by mouse, the following menu will appear.
|
|
|
|
From the menu you can quickly run the program (if needed, as Administrator) and view the Log file of the program.
Besides of quick starting BestCrypt DataShelter program, the System Tray Icon displays informational messages of the program:
- When you change policy for the protected folder, the following window appears:
|
|
|
|
You can click the Log File reference link to view more detail about the event in the BestCrypt DataShelter LogViewer program.
- When BestCrypt DataShelter denies some program from accessing the file in the protected folder, the following notification window appears.
|
|
|
|
You can click the Log File reference link and find the log string corresponding to the event of not granting access for the program attempting to read the file in the protected folder. Then, as the chapter Log file explains, you can run the Analyze access grant command for the log string and find out what the rule in the protection policy caused the event.
- As the chapter Creating policy based on folder access history explains, you can create the protection policy from the history of accessing the folder by programs. You can ask the program to accumulate the history and then review it after some time, for example, after a couple of days. When will it be the time to review the history, BestCrypt DataShelter system tray icon will show you the following notification.
|
|
|
|
- As the chapter Encrypted backup of the folder explains, you can create encrypted and compressed backup archive file for the protected folder. Besides, you can make BestCrypt DataShelter notifying you regularly (monthly, weekly, daily) about updating the backup archive. When will it be the time to update the archive, BestCrypt DataShelter system tray icon will show you the following notification.
|
|
|
|
- BestCrypt DataShelter monitors the way of accessing files in the protected folders. The program can detect an abnormal activity of some processes, for example, when the sign of ransomware activity detected. If it happens, BestCrypt DataShelter can terminate the process momentarily. In this case the following notification appears.
|
|
|
|
- BestCrypt DataShelter remembers the history of running processes. The history includes the hash (or secure checksum) of the executable files. If such a file is modified, in some cases it may mean that it is infected. When BestCrypt DataShelter detects a modification of some executable file and the corresponding program accesses a protected folder, the program notifies the user and temporarily denies access to the folder for the program. In this case the following notification appears.
|
|
|
|
As you see, with the notification dialogs of the System Tray Icon, BestCrypt DataShelter allows the user to manage accessing the protection folders easier, as well as to keep an eye on reviewing access history of the folder and saving the backup data.
See also: