Log file
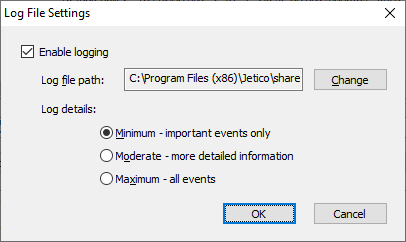
BestCrypt DataShelter writes information about events happened with protected folders to the log file. To choose location of the log file and amount of information written to the file, click the More... button in the main window of the program and run command Log file settings from the appeared menu. The following window will appear.
|
|
|
|
To choose location of the log file check the Turn on logging events checkbox and click the Browse button. Select Maximum, Moderate or Minimum option to choose should the log file contain all or only important events.
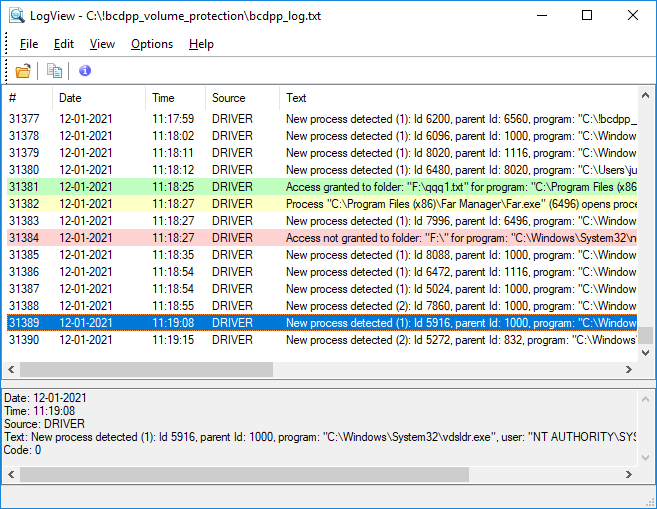
To view contents of the log file, run command View log file from the menu appeared after clicking the More... button in the main window of the program. You can also view the log file by running the command from the System Tray Icon. The following dialog window showing contents of the log file will appear.
|
|
|
|
The window above illustrates main events reported by BestCrypt DataShelter:
- New process running on the computer and interprocess communication
- The event of granting access to the protected folder for some process
- The event of not granting access to the protected folder for some process
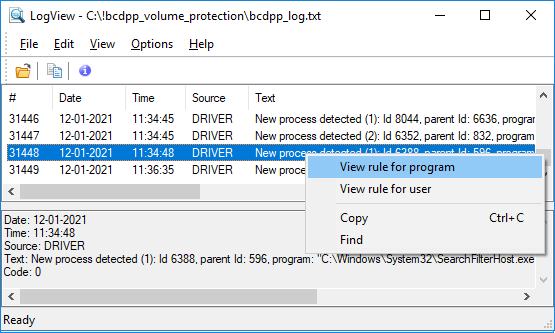
If you select some string and click the right mouse button, you will get context menu with commands specific for the log string selected.
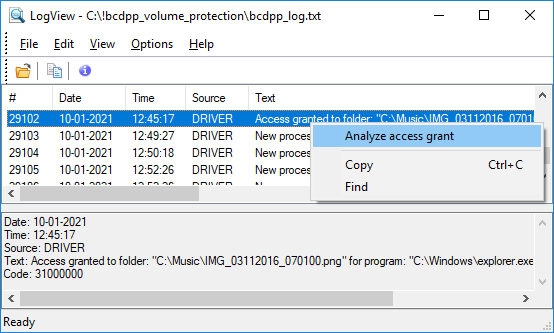
Click on the log string about new process detected by the right mouse button and the following context menu will appear.
|
|
|
|
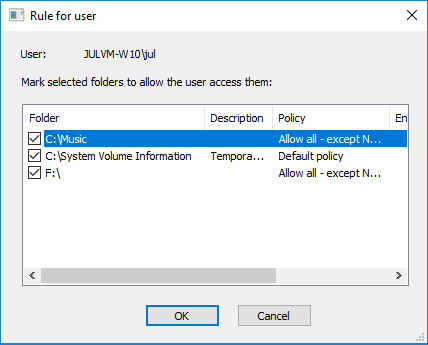
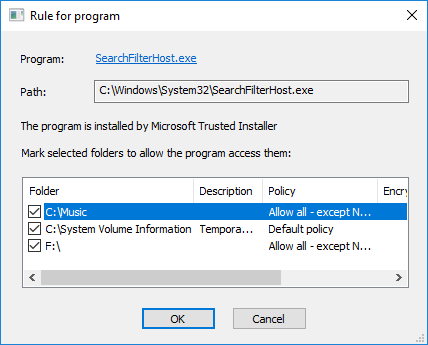
The log string reports about the program running and the user who has run the program. The commands from the context menu allows you to view the list of protected folders the user and the program can access, as the following pictures illustrate.
|
|
|
|
|
|
|
|
In the example shown in the pictures above, you may see that the program SearchFilterHost.exe and the user JULVM-W10\jul have a right to access all the protected folders (C:\Music, C:\System Volume Protection, etc.), because all the check marks are set for all the folders in the lists.
If you decide that the program or the user should be denied from accessing some protected folder, you can unmark the folder in the list. BestCrypt DataShelter will correct corresponding policy for the folder according to the check mark you have set or reset.
If you click on the log string informing about granted or not granted access to the protected folder by right mouse button, the following context menu will appear.
|
|
|
|
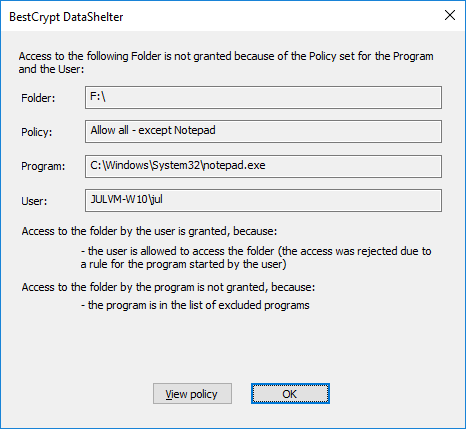
If you run the Analyze access grant command for the log string, BestCrypt DataShelter will show the dialog window that explains what protection policy caused the action and why the program was granted or not granted access to the folder. For the case when the access was not granted, the following window can appear.
|
|
|
|
For the example above, although the user JULVM-W10\jul has a right to access the folder, he/she was not able to do that with program C:\Windows\System32\notepad.exe, because the program is in the list of excluded programs in the protection policy with name Allow all - except Notepad.
If you click the View policy button, the program will show you dialog window with the detailed settings of the protection policy. Click the Ok button to close the window.
As you see, log viewing program in BestCrypt DataShelter not only lists events happened with the protected folders, it also allows correcting and tuning rules for the programs and users.
See also: