What is BestCrypt DataShelter
The chapter explains what BestCrypt DataShelter protects and how it performs that.
BestCrypt DataShelter allows access to files in selected folders only to trusted programs and users. To understand the protection better, let us list what undesirable things can happen to our documents:
- Documents are stolen:
- someone has got remote access to my computer and downloaded the documents
- someone has got physical access to the computer and made a copy of the documents
- Documents are modified:
- the computer is infected by ransomware and the documents are now encrypted so that you cannot access them
- the computer is infected by trojan and someone else reads and/or modifies the documents remotely
- documents are damaged because of the hardware problems
Let us imagine a simple scenario when I am a designer and have a folder with files of the PDF type that I am editing with the Photoshop software. For such a folder I can create a policy when only the Photoshop process has a right to access the folder. So if any other program would try to access the files, it will not be able to do that. It should prevent viruses and trojans from attempts to steal or modify the files.
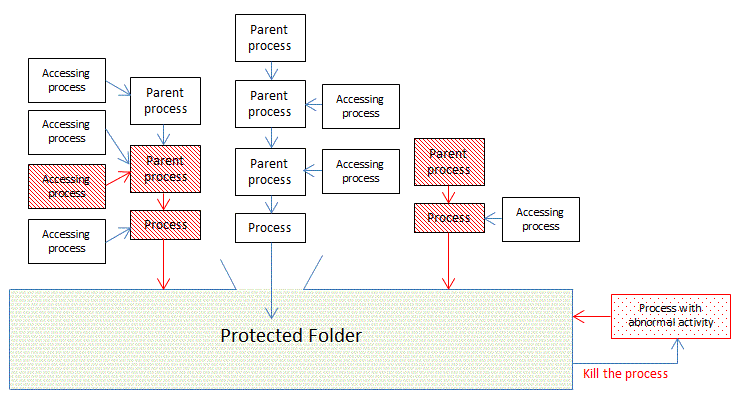
In practice, everything is a little more complicated. The Photoshop program does not start by itself. There is a parent process that runs the program, like some operating system module. Instead of the legal module, it can be a trojan software trying to inject its own code at the child Photoshop process. Even when the Photoshop process runs, another process can access it and do something wrong. The picture below illustrates how processes in the system communicate and what kind of analysis BestCrypt DataShelter should perform.
|
|
|
Figure 1. Processes accessing protected folder |
As the picture illustrates, BestCrypt DataShelter has knowledge not only about the process that accesses the protected folder but also about a whole chain of parents of the process. Besides, the software remembers the processes that communicate with all the chain of the processes.
What is important, BestCrypt DataShelter has not only a momentary snapshot of the processes running in the system but also keeps the history of the processes communications. For example, if the trojan runs for a fraction of a second, infects some other process and exits, the communication with the trojan will be remembered. Even more, the history of communications remembered even if the computer reboots or turned off. BestCrypt DataShelter accumulates the knowledge to prevent attacks better and, what is not so obvious, to create a specific policy for the folder protection easier.
Based on the policy selected for the given folder, BestCrypt DataShelter decides what process is allowed to access files in the folder and what processes are not allowed. If not allowed process attempts to read the file, it simply encounters "Access denied" error. It is rather normal and should be expected by any program because there are many other reasons (like lack of privileges) why the attempt to access the file can be rejected.
Besides that, BestCrypt DataShelter also monitors what the process is doing with the files it opens. There is some activity in the protected folder that BestCrypt DataShelter treats as abnormal. In this case, BestCrypt DataShelter momentary terminates the process. For example, this kind of monitor helps to prevent activity of ransomware in many cases.
Please note that there are other more traditional approaches to mitigate the threats. Antiviruses analyze running processes and detect the code containing harmful functionality. Firewalls monitor network traffic to prevent unauthorized access to the computer. The antivirus database with the virus stamps should be up-to-date, as well as the attack detection triggers in the firewall. BestCrypt DataShelter does not replace the functionality, it concentrates on protecting selected folders by limiting and analyzing processes allowed to access them. The software builds its knowledge database of what is good and bad from the actual processes and their communications. With this knowledge, the user can protect the most valuable files.
BestCrypt DataShelter prevents the risk of accessing the data if the hard disk drive with the data is removed and then inserted into another computer. Or, if the attacker loads another operating system on the computer. Such an operating system will not have antiviruses and firewalls or any other software protecting the data. The only way to prevent the attack is to have the data encrypted. BestCrypt DataShelter allows the user to encrypt physical disk volume where the protected folders are stored with a single button click.
With BestCrypt DataShelter the user can create encrypted and compressed backup archives of the protected folders. Once created, the software can regularly synchronize the contents of the backup archives with the corresponding folders. A single self-extracting executable file with encrypted data can be created from the backup archive file so that the data can be extracted on any other system even without the BestCrypt DataShelter software installed. Of course, if a proper password for the encrypted data is provided.