Protection policy overview
Chapter Using BestCrypt DataShelter explains that the Protection policy for the folder is the set of rules that allows or forbids some users and programs from accessing data in the folder. The chapter also explains two approaches in creating such lists of the users and programs:
- Allow all users (programs) access the folder, but create Exclude List of the users (programs) that are not allowed to access the folder
- Forbid all users (programs) access the folder and create a list of the users (programs) that are allowed to access the folder
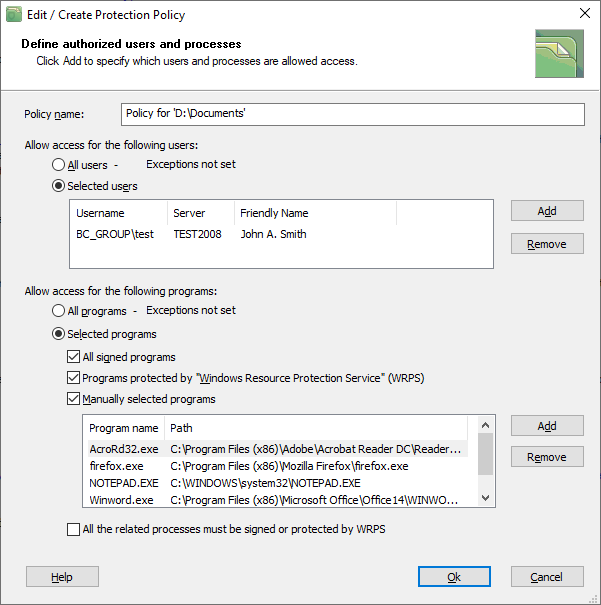
The following picture shows a dialog window for utilizing both approaches in creating the lists of the users and programs.
|
|
|
|
Selecting users for the policy is an easy process. To allow only a few users to access the folder, choose the Selected users option and click the Add button. The program will show you all the users registered on the computer, select some of them and click the Ok button.
If you wish to use the approach when all the users are allowed to access the folder, choose the All users option. To set the Exclude List of the users (programs) that are not allowed to access the folder, click the Exception not set link as the picture below illustrates and select the users for the exception list.
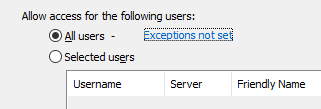
The same way works for the list of programs to be allowed to access the folder. You can allow all the programs to access the folder and set the list of exceptions. Or, you can explicitly select the programs that are allowed to access the folder.
Since your computer may have dozens (if not a hundred) programs installed (including operating system utilities), selecting the programs can be a more difficult task than choosing among few users to allow them to access the folder. Fortunately, BestCrypt DataShelter has a number of means to create the list of programs without analyzing every program on your computer.
- Creating the list of the programs manually. Select the protection policy in the main window of the program and click the Edit/Create button.
The dialog window as shown above will appear. Click Selected programs and now decide how restrictive your policy should be: - If you have only Microsoft Word documents in the folder, click the option Manually selected programs and choose only Winword.exe program. Add few others like Notepad.exe if you have text files in the folder.
- If you want the operating system utilities like File Indexer also accessing the files, you can set the All signed programs and Programs protected by "Windows Resource Protection Service" (WRPS) options too. Microsoft Windows has a Secure Signing feature for executable files. It means that the programs from respectable vendors (including the Microsoft ones themselves) are signed by the Microsoft certificate. If you set the All signed programs, BestCrypt DataShelter will validate a secure signature of the executables accessing the folder, including the Microsoft components of the operating system.
- Option All the related processes must be signed or protected by WRPS is the most sophisticated. BestCrypt DataShelter monitors communications between processes, as it is shown in the What is BestCrypt DataShelter article. The program becomes aware of parents and grandparents of the process. It detects events of opening the process by other processes. So if you allow some program to access the folder, by setting the option you will also require that all the interprocess communications with the program would happen only with trusted signed programs.
- Create a list of programs by looking at the types of files in the folder. You can ask BestCrypt DataShelter to scan all the files in the folder, create a list of file types, and list programs that are registered in Windows for opening the files. For example, Microsoft Word is registered to open *.Doc files and Adobe Acrobat Reader to open *.Pdf files. BestCrypt DataShelter will list the programs and you will get the protection policy ready: you can continue working with the files as usual while access from the other programs will be denied. Read the article Creating policy based on file types for more detail.
- BestCrypt DataShelter can also create a list of programs from the history of accessing the folder by programs. The idea is in the following. You select the folder and set a protection policy for the folder that allows all the programs to access the folder in a normal way. You work with the files in the folder as usual for some period (hour, day, week). All that time BestCrypt DataShelter monitors what programs access the folder. Then you command to list all the programs and include them in the list of allowed programs for the protection policy. After that, any new program that would try to access the folder will be denied. So if any trojan infects your computer, it cannot access files in the folder. Read the article Creating policy based on folder access history for more detail.
BestCrypt DataShelter is an interactive program. It informs you when some program is rejected from accessing files in the folder in the System Tray Icon messages. Besides, you can always take a look at the Log File and correct the list of programs in the policy.
See also:
Creating policy based on file types