Creating policy based on folder access history
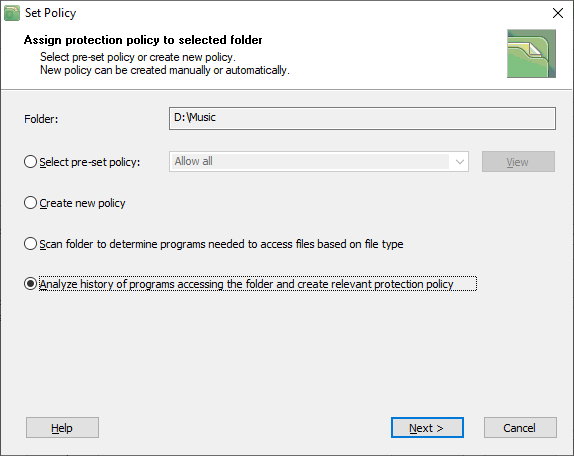
Chapter Properties of the protected folder describes how the user can define a protection policy for the folder. To do that, click the Properties button in the main window of the program and then click the Set policy button in the Folder Properties dialog window. BestCrypt DataShelter will show the following dialog window.
|
|
|
|
BestCrypt DataShelter can create a policy based on the history of accessing files in the folder by programs. For example, if you know that your computer is not infected by trojans, you may decide that all the programs that access the folder should be trusted. If so, you can create the protection policy based on the folder access history. Select the option Analyze history of programs accessing the folder and create relevant protection policy and click the Next button. The following window will appear.
|
|
|
|
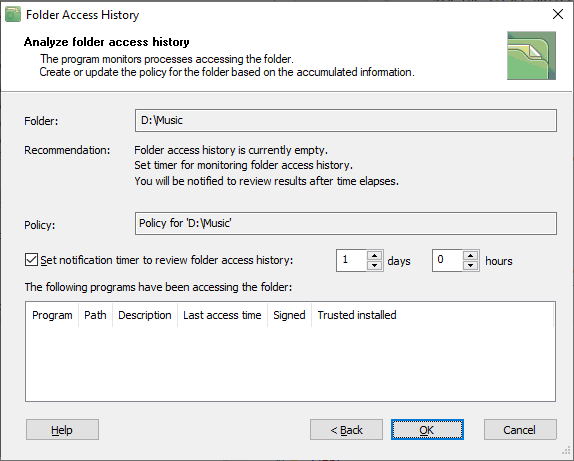
The window above shows that when you have just added the folder to the list of protected folders, the list of The following programs have been accessing the folder is empty. BestCrypt DataShelter will start gathering the information as soon as you click the Ok button. At the same time, the program suggests the user should choose the option Set notification timer to review folder access history. The user can choose a period of several days or hours when the program reminds about reviewing the list of The following programs have been accessing the folder again. For example, if you choose one day and click the Ok button, the program will start gathering the history information and after one day it will show you the following dialog window in the System Tray area of the desktop.
|
|
|
|
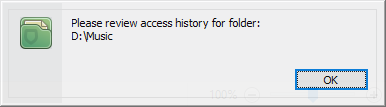
Click the Ok button in the notification window and BestCrypt DataShelter will show you the dialog window with all the programs that accessed the folder since the time you have added the folder to the list of protected folders, as the following picture illustrates.
|
|
|
|
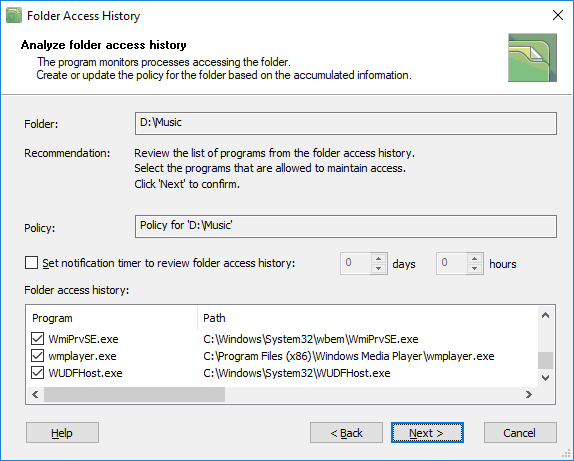
You can review the list of programs that accessed the folder and decide that you do not want some program to access the folder. In this case, reset the checkbox for the program in the list of The following programs have been accessing the folder list in the dialog window.
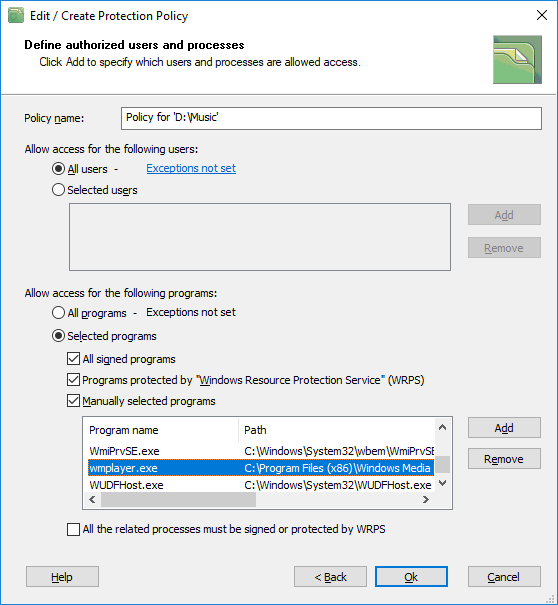
Now if you move forward and click the Next button in the Folder Access History dialog, the program will display the same dialog window that appears when you create a protection policy manually. You will see that now the policy for the folder includes the list of The following programs have been accessing the folder and it has recommended options set, as the following picture illustrates.
|
|
|
|
Click the Ok button and BestCrypt DataShelter will save and apply the policy for the folder.
Please note that BestCrypt DataShelter always accumulates the information about programs accessing protected folders, whether you initiate the process described in the article, or not. For example, you can create a simple policy for the folder and after some time decide to review the folder access history information. In this case, the Folder Access History dialog window will already contain information about the programs accessing the folder. You can use the information to update the policy for the folder.
See also: