Central Management of BestCrypt Volume Encryption
After the successful deployment of BestCrypt Volume Encryption (BCVE) on remote computers, an administrator can manage BCVE on client computers through Jetico Central Manager Console (see below):
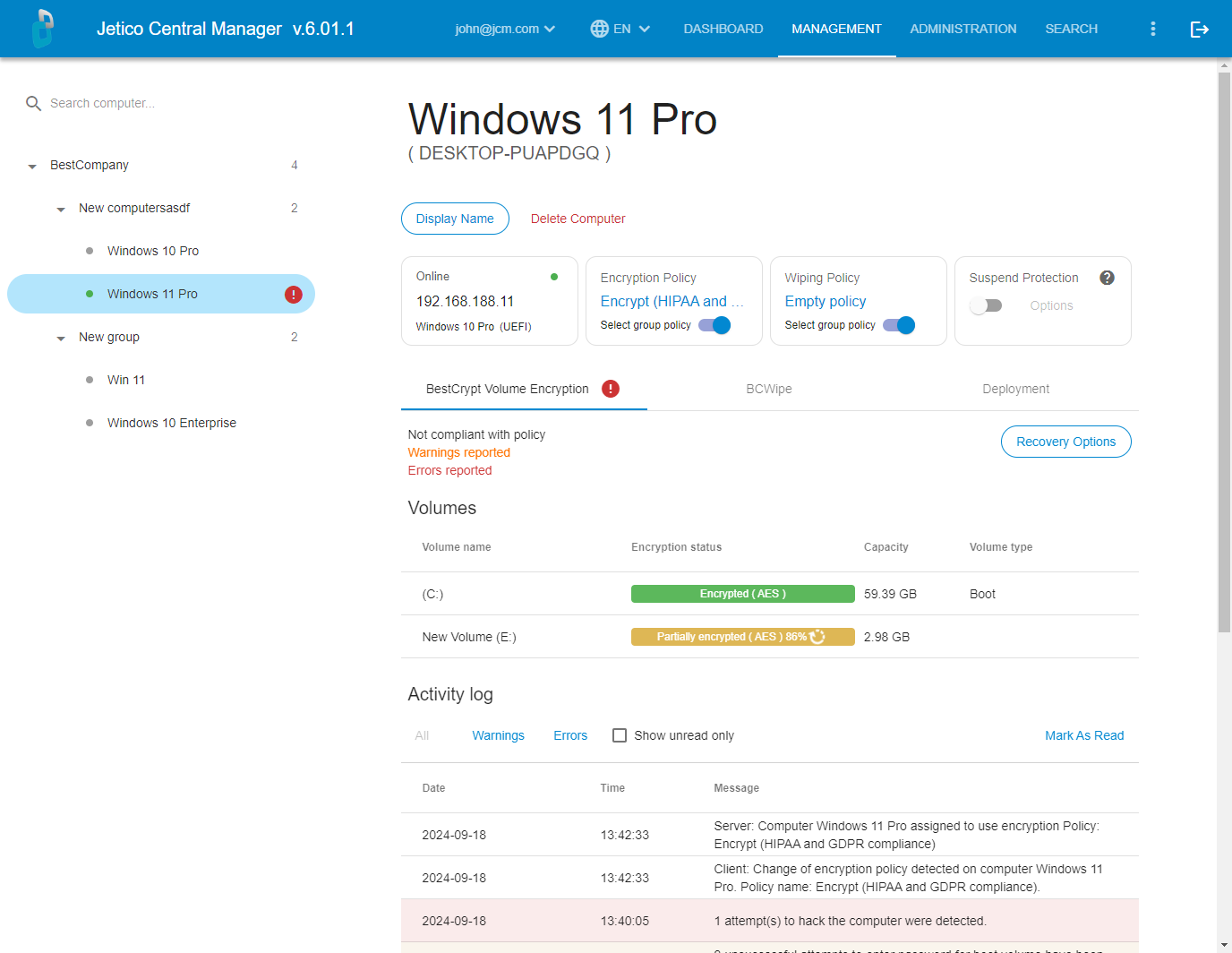
Jetico Central Manager Database receives and displays the following information from BCVE program running on the client computers:
- Information about all disk volumes (partitions) on the computer including sizes, labels, and volume types
- Status of every disk volume (encrypted/partially encrypted/not encrypted/error)
- Log information about BCVE events (encrypting/decrypting volumes, installation of new disk volumes, volume errors, etc.)
- Rescue information about all encrypted volumes.
Additionally, the administrator can click Recovery Options to prepare rescue file or rescue bootable disk to recover encrypted disk volume on the selected computer. See the section of this manual entitled Rescue procedures in Jetico Central Manager for more details about how to recover encrypted disk volumes on client computers.
Distributing encryption policies.
The administrator of JCM Console can manage encryption policy on client computers by assigning a policy to the whole group, or to selected computers.
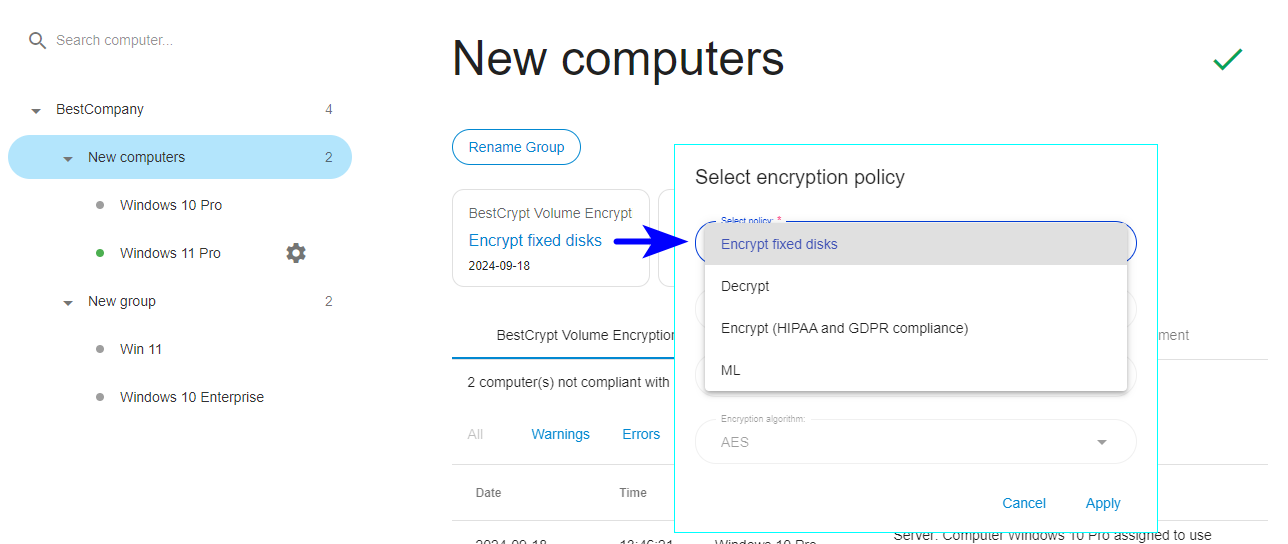
- To assign an encryption policy to a group:
- Select the group name in the left panel
- Click on the current encryption policy name
- The Select encryption policy dialog box will appear
- Open the drop-down list of existing policies
- Choose the required policy and click Apply
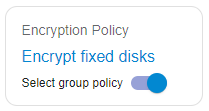
- To assign an individual policy to a client computer:
- Select the computer in the left pane, disable the "Select group police" toggle switch:
- The dialog Select encryption policy will appear
- Choose the required policy and click Apply
Computers with individual policies are marked with the 'gear' icon in the list of computers: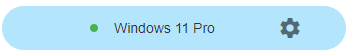
If the assigned policy forces the client software to encrypt fixed disks (in the policy, Fixed drive action = Encrypt), BCVE will ask the user on the client computer to enter a password to encrypt the volumes. The encryption will start and will be performed in the background. The process can be stopped, but it will be automatically resumed after a short time or after reboot. As soon as the encryption process starts, the user will be prompted to enter the password at boot.
NOTE: The automatic encryption may NOT start (or not resume) for the following reasons:
1. The client computer was not rebooted after installation.
2. BCVE main window has been opened on the client computer.
3. The client-server connection has been lost.
Suspend Protection
The administrator can temporarily suspend client protection (i.e. remove boot-time authentication). In these cases, the volumes will remain encrypted but accessible without a password. This feature may be required to allow the computer(s) to restart automatically (Windows Updates, backup purposes, etc.). The feature is especially necessary when managing servers that are required to function around-the-clock.
ATTENTION! The option Suspend protection exposes a security risk. For example, someone can turn off the computer, take it out of the company's network, turn it on again and gain access to the data. Remember to disable this option as soon as automatic reboot is no longer required.
By default, Suspend Protection disables boot-time authentication for all of the following: power on, resuming from hibernation, restart. This can be limited by clicking Options hyperlink that appears next to Suspend Protection checkbox when it is set. The following options are available:
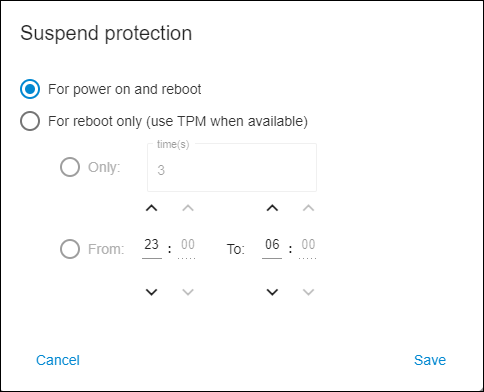
- 🔘 For power on and reboot - default option
- 🔘 For reboot only (use TPM when available)
This setting will disable boot-time authentication for restarts, while entering encryption password will still be required when powering on or resuming from hibernation.
NOTE: Available for UEFI computers only. If selected computer is MBR, this option will be grayed out.
The following sub-options allow limiting restarts with no authentication to a specific number of times or hours:
- 🔘 Only: X time(s) - choose how many times encrypted computer is allowed to restart without boot-time authentication.
- 🔘 From: XX:XX to: XX:XX - choose during which hours encrypted computer is allowed to restart without boot-time authentication.
If a properly configured and ready-for-use TPM is found on subject computers, it will be added as a secure storage for the encryption key during restart. Read more: How to configure TPM for BestCrypt Volume Encryption
As soon as Administrator enables Suspend Protection, it will be indicated in Activity Log area as follows:
Server: Suspend Protection set for computer 'computer name'
After that, if the client computer is Online, another message in Activity Log is expected:
Client: Suspend Protection set for computer 'computer name'
If the client computer is Offline, it will receive the setting and send the log message to the Console after it's connected again. Upon receiving this confirmation from the client, boot-time authentication is removed.
As soon as Administrator disables Suspend Protection, two records appear in the Activity Log:
Client: Suspend Protection unset for computer 'computer name'
Server: Suspend Protection unset for computer 'computer name'
At this point, the boot-time authentication is restored.
Computers with 'Suspend protection' option enabled are marked with the 'pause' icon in the list of computers:
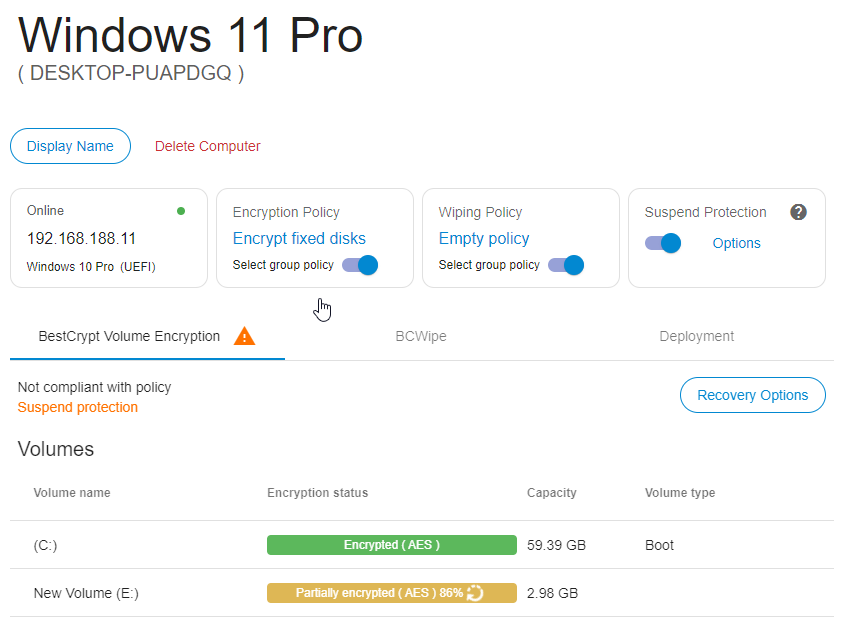
Furthermore, computer status for such computer is set to 'yellow' on the computer page, and the warning is posted:
Pre-boot password environment
To protect endpoints from unauthorized access once encrypted, BestCrypt Volume Encryption prompts for password every time the endpoint is powered on or resumes from hibernation, before the OS even starts to load. The appearance of this password prompt environment is fully customizable.
The following two modes of the password environment are supported:
- Boot-time Prompt for Password in Text Mode - default option; suitable for any endpoint, both newer generation EFI and Legacy; only the text can be customized
- Boot-time Prompt for Password in Graphical Mode - suitable for newer generation EFI endpoints only ; text and images can be customized, supports logo customization.
Boot-time Prompt for Password in Text Mode can be centrally managed from the Jetico Central Manager console. The controls are described in detail in the following article: Company Settings
Boot-time Prompt for Password in Graphical Mode can be pre-configured one endpoint and then exported and applied to all client endpoint in the following way:
- Create and activate a desired boot-time GUI theme. Here is how: Boot-time Prompt for Password in Graphical Mode
🗲HINT: To unlock the "Boot-time prompt for password" command from the Password menu on the client computer, assign an encryption policy with "Manage Locally" under "Fixed drive action" and run BestCrypt Volume Encryption 'as Administrator'.
- Locate the export_gui_theme.exe utility in the media.out\installer sub-folder of the Jetico Central Manager home directory and copy it to the endpoint from step 1.
- Launch Command Prompt 'as Administrator' and run the following command:
> export_gui_theme.exe -P'<full_path_to_output_folder>'
Notes:
1. The output folder must exist;
2. Single comma quotation marks ( ' ) are necessary.
Sample:
> export_gui_theme.exe -P'C:\tmp folder\'
Completing the work, the program creates the set_graphic_theme.exe application in the output folder specified. - To activate the exported theme on another endpoint, copy set_graphic_theme.exe to any folder on the that endpoint and run the executable file as Administrator.
🗲HINT: To activate the exported theme on multiple endpoints in bulk, use the executable file with PowerShell or a deployment automation tool of your choice.
See also:
BestCrypt Volume Encryption on Client Computers