Rescue Procedures in Jetico Central Manager
The Jetico Central Manager (JCM ) Database stores recovery information for disk volumes (partitions) encrypted on remote client computers with BestCrypt Volume Encryption (or BCVE) software. The JCM administrator has to follow several steps to retrieve the required information:
How to recover a computer that does not boot or repair a fixed volume:
- Select the client computer in the list, click Recovery Options on the computer page. The following window appears:
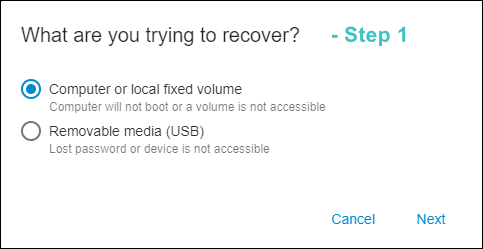
- Choose the first option and click Next to get the next window:
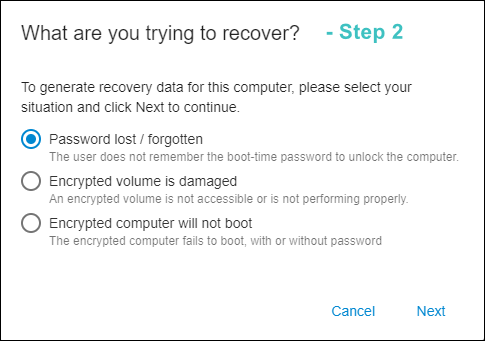
- Choose the appropriate option:
- Choose the first option, if password for the encrypted computer has been lost. Decryption is not required in such a case; a recovery password will be automatically generated by the program which can then be used to boot the computer.
NOTE: After booting the computer with the recovery password, it is possible to change the password on the client computer using the menu command:
Rescue-->Recover/Change Boot Password
NOTE: For Mac computers with T2 chip, JCM Server stores the system Recovery Key, that can be used to reset the encryption password if required. Other rescue functions are not available.
- Choose the second option to repair a non-system volume. The program will generate a Rescue File. The file can be generated with the same password that was used to encrypt the volume, or with a new password. The following window provides this option along with detailed instructions on how to use the Rescue File:
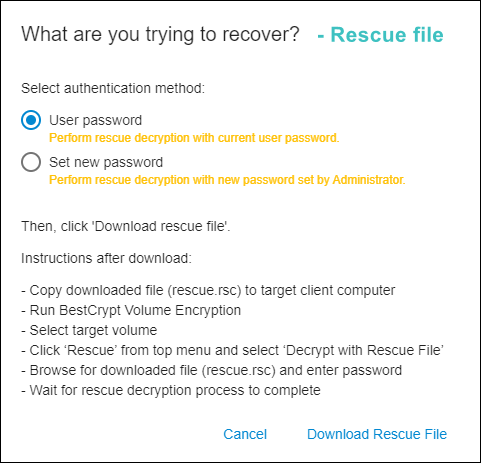
NOTE: For Mac computers with T2 chip, rescue functions are available only for non-apfs volumes.
- Choose the third option to recover the client computer that will not boot. In this case, a bootable USB disk is created that can be used to boot the computer and run rescue decryption. The following window shows the detailed instructions:

How to recover encrypted removable USB drive.
- Select any client computer in the list and click Recovery Options on the computer's page. The following window will appear:
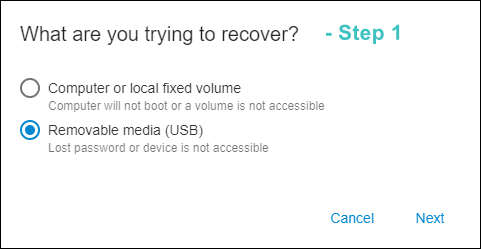
- Choose the second option and click Next to get the next window:
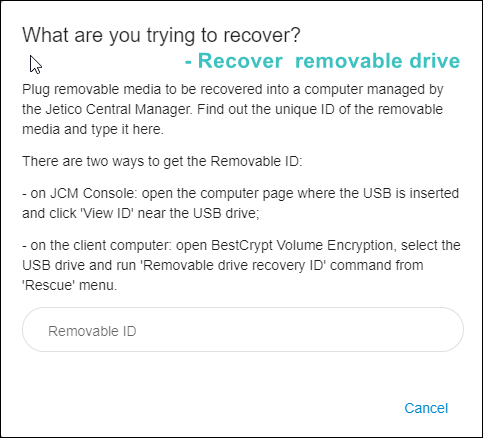
- Follow the instruction to get the ID for the corrupted USB drive.
Note: you can locate the cursor inside the ID field and press Spacebar, the program will display a list of all IDs registered in the database. Choose the appropriate ID.
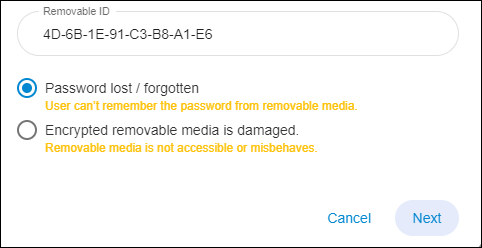
- Choose the option that corresponds to the issue at hand - either the password has been lost or the removable device has been corrupted - and click Next. If a password has been lost, decryption is not required, just use the new password to mount the encrypted removable disk. In the case of a corrupted removable drive, a Rescue File will be created in the same manner as in the case of an aforementioned corrupted fixed volume.
See also: