Simple Interface
BestCrypt Volume Encryption v.4 introduces a new-style user interface that allows setting up protection in just one click. The new interface is ideal for people who:
- want to securely encrypt the whole computer
- don’t have time to study details of encryption process
- need to encrypt computer once and to forget about security problems for a time being
Those who need advanced encryption options can easily switch user interface from Simple mode to Advanced.
Interface overview
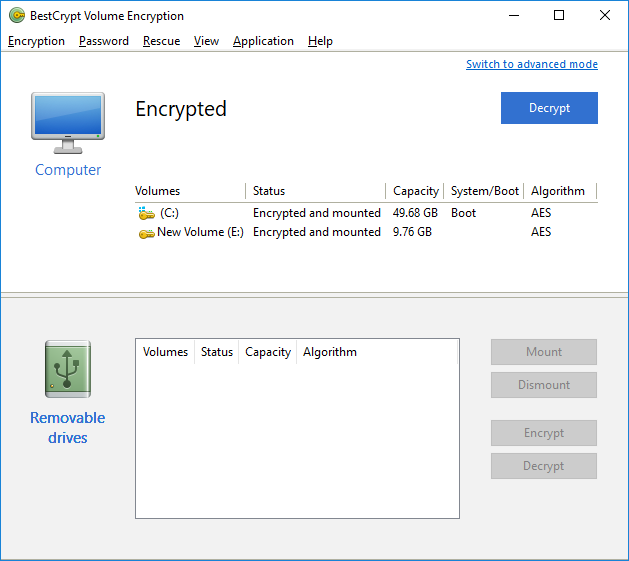
The main application window is divided in two parts. The upper part (also referred to as a Computer Pane) provides detailed information about current encryption status of the computer and its volumes and the control to start / resume the encryption process. The lower part (the Removable Drives Pane) displays the list of available removable devices with the controls to manage encryption on / access to a selected media.
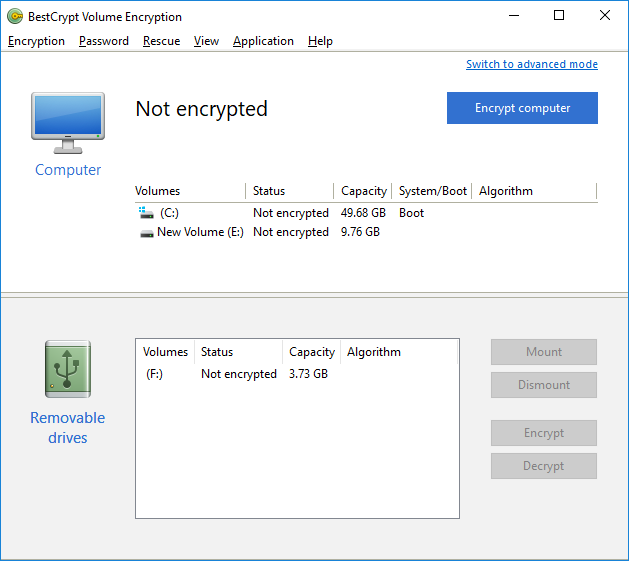
The lower part can be hidden by using the splitter:
All the commands are available from the application menu at the very top of the application window.
Encrypting the computer
To encrypt all volumes on the computer and enable boot-time authentication, click Encrypt computer. You will be prompted to choose an encryption algorithm and an encryption password:
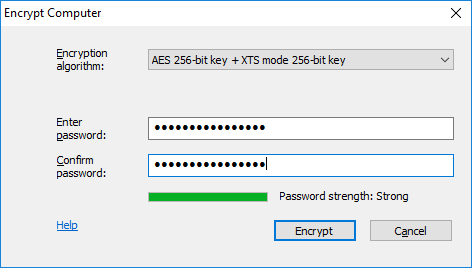
Click Encrypt to initiate the encryption process. The process will start encrypting the data on the volumes located on the fixed disks of the computer, one by one. The boot-time password protection is enabled immediately after the encryption process is started. The progress of the encryption will be reported in the window opened:
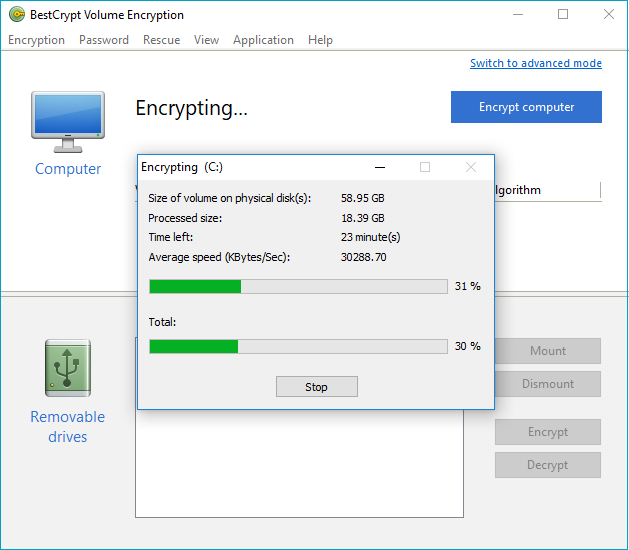
The upper progress bar shows the progress for the volume that is currently being encrypted. The lower progress bar shows the total progress for all volumes on the computer.
The encryption process is fully transparent. The computer can be used normally during encryption. Clicking Stop on the progress window will pause the encryption process. To resume the process, click Resume encryption in the right upper corner of the Computer Pane.
The computer will have a Partially encrypted status until the encryption process finishes. When it does, the status will change to Encrypted.
Switching to Advanced mode and back
The set of basic encryption functions provided in the Simple interface is designed to fully cover the standard protection needs. Additional functionality for a more flexible control over the encryption configuration is available from the Advanced Interface. This includes e.g. encrypting selected volumes only, moving encryption key to removable a device, connecting a TPM. More information on the features of the Advanced Interface is available in this article: Using BestCrypt Volume Encryption.
To switch to the Advanced Interface, select Application menu item and click Switch to Advanced mode. Alternatively, there is a shortcut for this action in the top right corner of computer area. To switch back to the Simple Interface, select Application menu item and click Switch to Simple mode.
In Simple Interface all volumes are encrypted with the same password and are mounted automatically at boot time. In case if several volumes were partially encrypted from the Advanced Interface with different passwords, and then encryption is Resumed from Simple Interface, the program will bring all the volumes to a common password that will be asked at boot time. The user will be asked to enter password for each volume.
Decrypting the computer
When computer is fully or partially encrypted, the Decrypt button appears in the right upper corner of the Computer Pane. To decrypt the computer, click the button and enter the encryption password.
Working with removable drives
Every removable device with a supported file system plugged in to your computer will be listed in the Removable Drives Pane of the simple interface.
To encrypt a volume on a removable drive, select it from the list and click Encrypt.
To access the data on an encrypted removable drive, it should be mounted first. Select the encrypted removable volume from the list and click Mount. The volume will become accessible from Windows Explorer after you have provided the correct password.
NOTE:To access the data on an encrypted removable drive from another computer, this computer should have BestCrypt Volume Encryption or BestCrypt Volume Encryption Traveller software.
To remove encryption from an encrypted removable drive, select it from the list and click Decrypt. Wait for the decryption process to complete.
Rescue operations
For the cases when standard Decrypt command is not available (e.g. Windows fails to boot) BestCrypt Volume Encryption offers recovery decryption functionality. It is strongly recommended to create a Rescue Bootable USB (or CD) for your computer.
NOTE: The Rescue Bootable USB is computer-specific. The set of files created for one machine will not work to decrypt another machine.
To create a Rescue Bootable USB, select Rescue menu item and click Save rescue data. More details on the recovery procedures is available in this article: Overview of Rescue Procedures
See also:
Encrypting and Decrypting Volumes
Mounting and Dismounting Volumes
Moving Encryption Keys to Remote Storage
Rescue Bootable CD and USB disks