Moving Encryption Keys to Remote Storage
By default, BestCrypt Volume Encryption stores encryption keys for a volume on the same volume in encrypted form. The key is encrypted by another key derived from the password for said volume. To mount the volume, the user enters the password, the software then decrypts the key and then mounts the volume.
To enhance the security level of an encrypted volume, the user can move the key in encrypted form from the volume to some external storage. It may be a removable disk (like a USB stick) or Smart Card, or some Token device, like SafeNet eToken or a Yubikey device.
If you move an encryption key from a volume to a removable storage device, any person who wants to mount the volume will have to: a) know password for the key and b) have the removable storage device. Without either of these two factors, it will be impossible to get access to the data inside the volume (this is called as Two-Factor Authentication).
To move an encryption key from an encrypted volume, select it in BestCrypt Volume Encryption’s main window. The volume should be in mounted state. Run the command Encryption key -> Move key to external storage from the Volume menu. If the disk volume is not a boot or system volume, the program will ask the user to choose removable device to store the key. The following window will then appear.
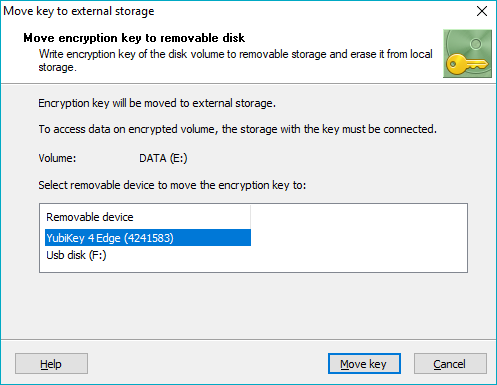
Select removable storage device from the list in the dialog window and click Move key.
If the encrypted volume is System or Boot, the software must run through a couple of additional steps to make use of the removable key storage as safe as possible. First, the software must verify that the removable device used to store the key can be accessed at boot time. Otherwise the program cannot read the key from the device and computer will not boot. The following window appears:
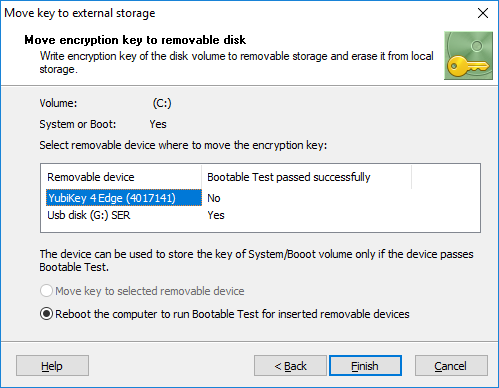
If the removable storage has not yet passed the boot test (as in the picture above using the YubiKey device), then the computer will be rebooted to run the test.
For Yubikey, the program will also check if the device was initialized for using on another computer. If yes - there are two options: erase all keys from this device or choose another device.
During reboot, the software will check whether the device can be read, or not. After reboot, run the command to move the key to the removable storage once again. Now the removable storage should appear in the dialog window as passed boot test. The column Bootable Test passed successfully should show Yes status for the device.
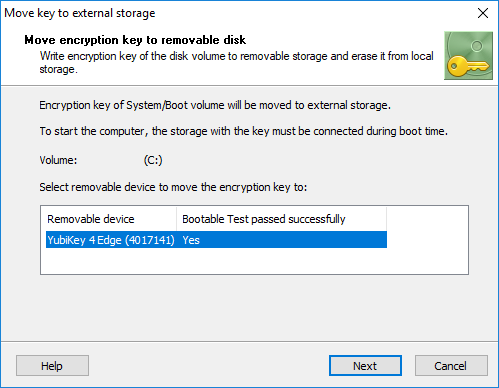
After that, the program will recommend the user to create a Rescue disk, or confirm that it has been already created. Then the encryption key will be moved to the external storage.
NOTE: for the Token devices, the operation of moving the encryption key is equivalent to the operation of changing password. The volume password is now equal to the token password.
As soon as the encryption key has been moved, the removable device must be plugged in for authentication every time you mount the encrypted volume. When the computer boots and password is required at boot time, the Token device has to be inserted before the password prompt appears.
To move the key back from the removable storage device, run the command Encryption key -> Restore key from external storage from the Volume menu. Please note that after restoring the encryption key back to the volume it will be possible to mount the volume with the same password as the Token device has.
It is recommended to make a backup copy of the device with the encryption key using the command Volume -> Encryption key -> Backup keys to other external storage. If you no longer wish to use removable devices to store any encryption keys, you can erase the keys from the device with the Volume -> Encryption key -> Delete all keys from external storage command.
See also:
Encryption Keys on Hardware Token