Keyfiles allows users to set another level of authentication for their containers, in addition to standard password protection.
Keyfiles are (optionally) set during container creation or when adding new password. User may choose one or several Keyfiles to secure the container. BestCrypt processes its' contents and generates a hash that is added to the encryption key. To mount a container encrypted with Keyfiles, user needs to provide correct password as well as the set of Keyfiles (the order does not matter).
Advantages of using Keyfiles:
Specially-designed Keyfile Manager
allows adding and viewing keyfiles easily.
The Manager is available by
clicking the button in advanced view of the Enter Password dialog:
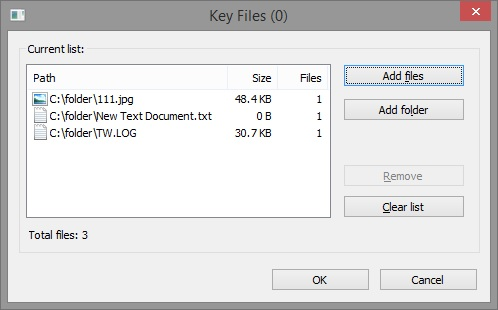
NOTE: If you add a folder, all files residing in that folder will be added, but NOT subfolders. If you add a file to the folder later, it will be impossible to open the container until you delete the newly added files.
NOTE: Basically any file can be used as a Keyfile with one requirement: it should not be modified. Once a Keyfile is modified (to be more exact, any bit of its first 1024 kilobytes), it becomes a new file, which won't allow you opening container anymore.