Creating a wiping policy
To create a wiping policy, click “Add new wiping policy” in the “BCWipe: Wiping policies” section of the Company Page. The following view will appear:
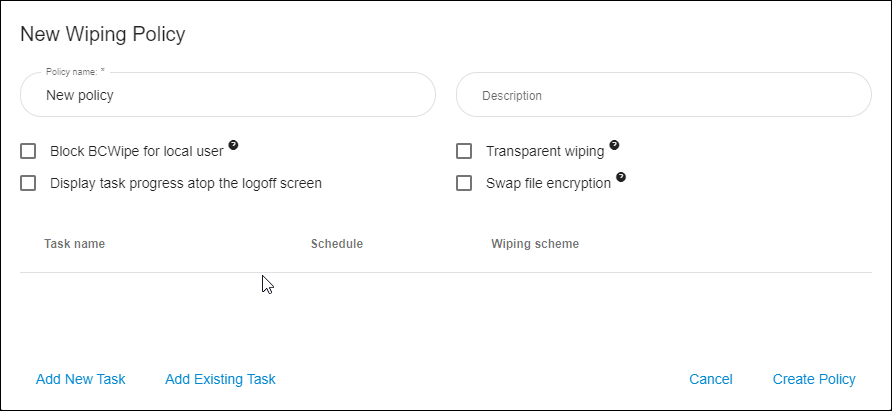
- Policy name — Choose a name for your new policy.
Description (optional): Enter a brief comment about the policy for your future reference.
🗹 Block BCWipe app for local users on client computers — When enabled, local users will be restricted from running any wiping tasks on their own. Instead, only tasks that are part of central policies can be performed.
- Policy tasks
This table lists all wiping tasks associated with the policy.
Add new task opens a dialog box to help you create a wiping task. Click for a step-by step guide on how to create a wiping task.
Add existing task allows you to assign any previously created tasks to the policy.
Find more detailed information on wiping tasks here: Wiping tasks
- Transparent Wiping
🗹 Enable — When Transparent Wiping is enabled, BCWipe will automatically wipe the contents of any file or folder that is deleted. Learn more about Transparent wiping here: Transparent Wiping overview
You can also configure these settings to use with Transparent Wiping:
Wiping scheme — Select a wiping scheme to be used when Transparent Wiping erases files.
🗹 Verify last pass — Enable post-wiping verification.
>Exceptions — Fine-tune Transparent Wiping by adding a list of exceptions. See more on this functionality here: Transparent Wiping overview
- Swap File Encryption
🗹 Enable — Windows uses a swap file to cache your most frequently accessed files.
Enable Swap File Encryption to protect traces of your sensitive data. Learn more about Swap file encryption here: Swap File Encryption (jetico.com)
You can also configure these settings to use with Swap File Encryption:
Encryption algorithm — Allows you to select one of the following encryption algorithms: Rijndael, Blowfish, GOST 28147-89, or Twofish.
🗹 Initialize with random data when your computer is turned on — Check this option to enable the overwriting of any data that was swapped before encryption was enabled.