JCM provides a convenient way for managing groups of computers. The first (default) group is created automatically by the setup program and is assigned the name New computers. This default group cannot be deleted. Newly added computers will appear in this group, unless the JCM Agent Setup file is launched with the special -G parameter.
There is no limit to the number of groups that can be created. However, the maximum number of computers in a single group is 100. Client computers can be distributed among these groups in any way deemed appropriate by the JCM administrator: by physical location, by required security policy, or by any other attribute. Both computer groups and the computers within each group are displayed in alphabetic order.
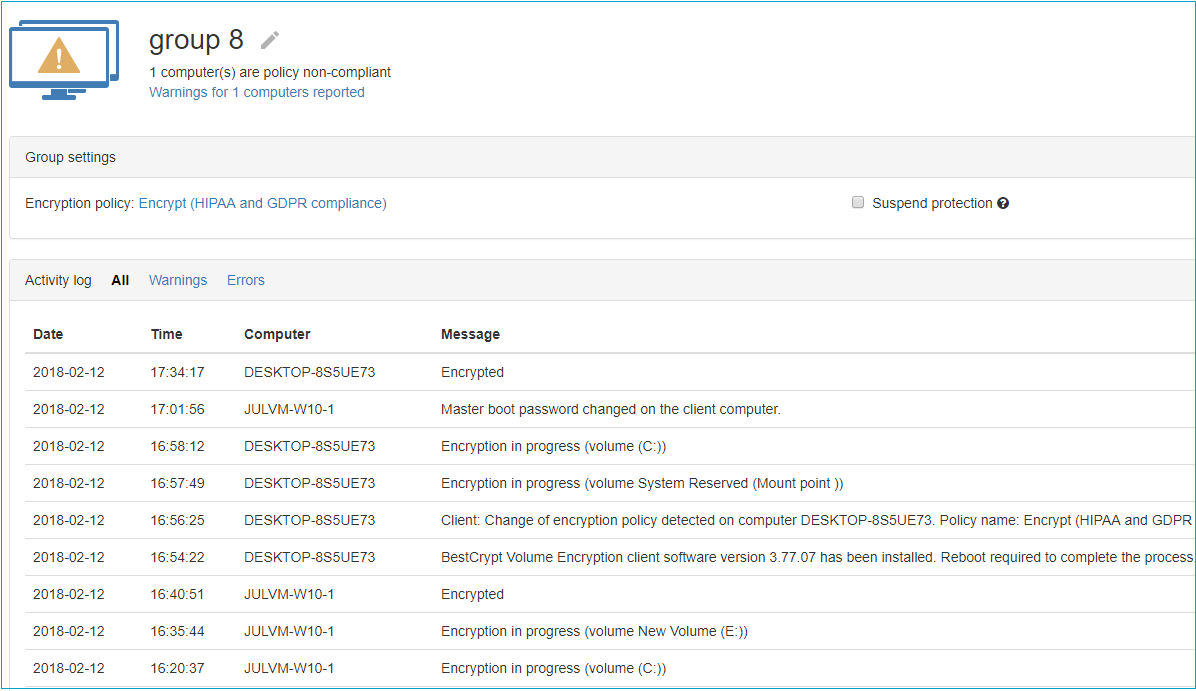
Encryption policy can be assigned to the whole group or through individual policies. A group policy is assigned on a Group page, while an individual policy is assigned on a Computer page. If an individual policy is assigned to a computer, the computer is marked with 'gear' icon in the list.
If a group is selected in the left list, the Group page is displayed in the right pane. It looks like:

The page is divided into three parts:
The Move function is available in the Computers and groups table on a company's page:
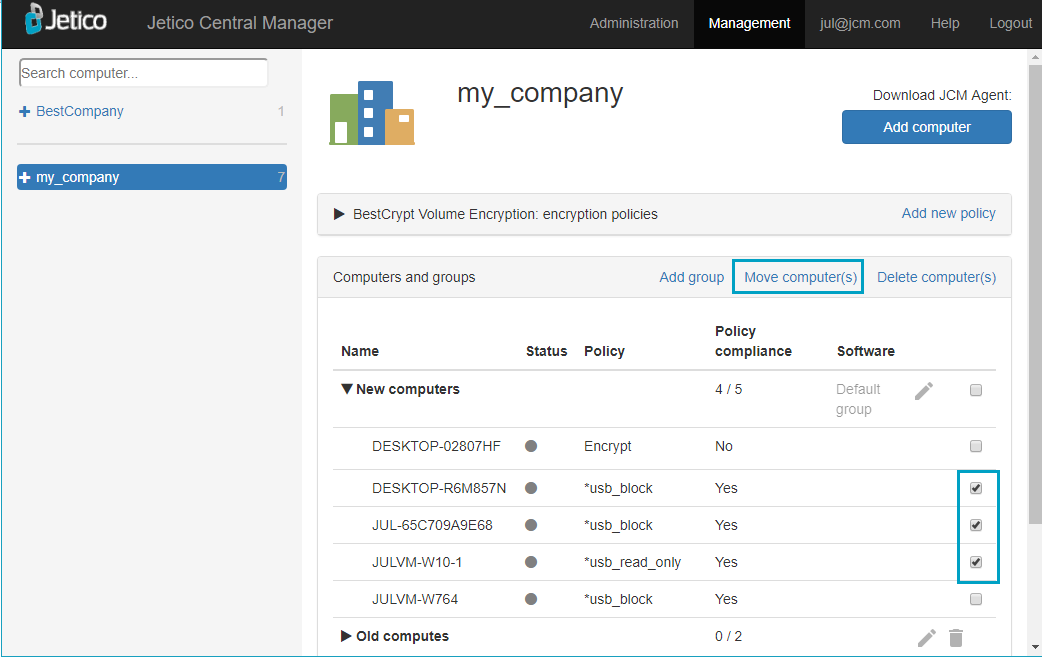
If a computer is moved from Group1 to Group2, the computer is automatically assigned the encryption policy of Group2. If the computer has already been encrypted and the 'move' operation would
cause a change of encryption algorithm, the user will be prompted to decrypt the computer first and then attempt to move the computer again.