Central Management of BestCrypt Volume Encryption
After the successful deployment of BestCrypt Volume Encryption (BCVE) on remote computers, an administrator can manage BCVE on client computers through Jetico Central Manager Console (see below):
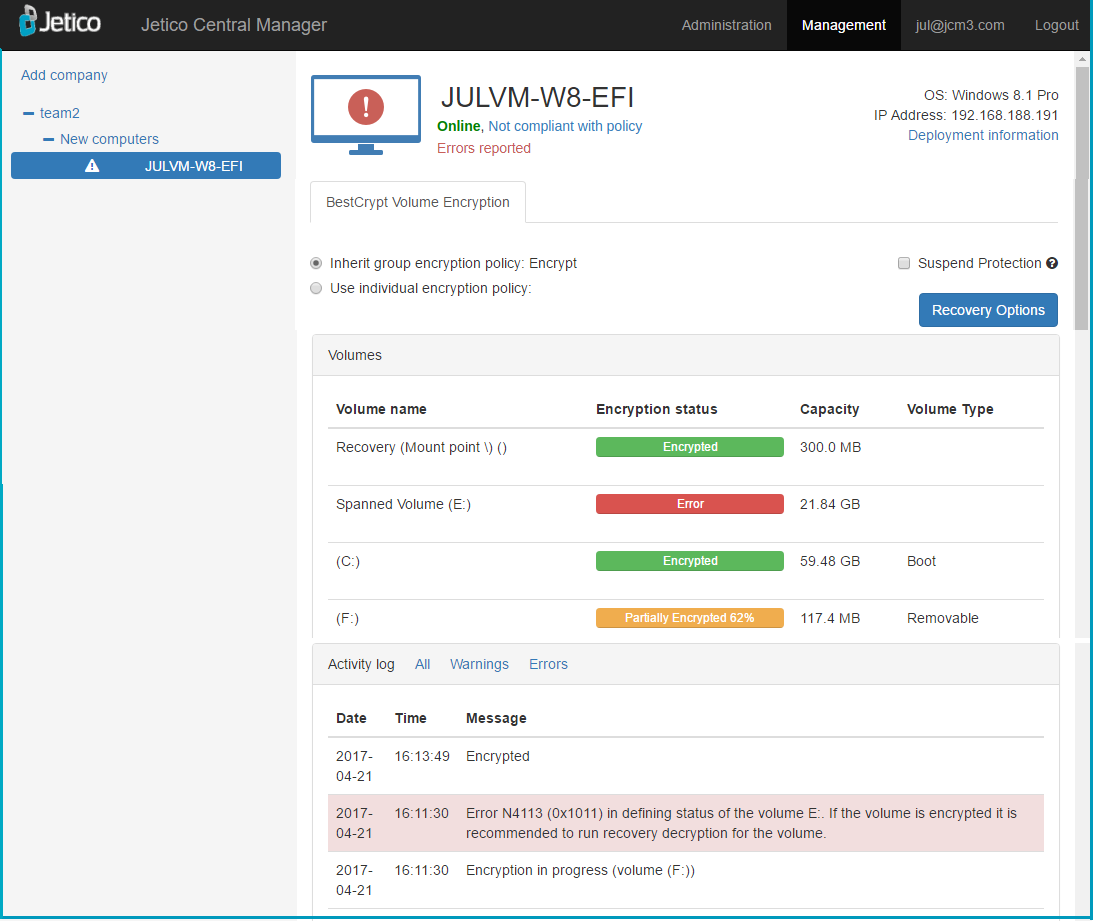
Jetico Central Manager Database receives and displays the following information from BCVE program running on the client computers:
- Information about all disk volumes (partitions) on the computer including sizes, labels, and volume types
- Status of every disk volume (encrypted/partially encrypted/not encrypted/error)
- Log information about BCVE events (encrypting/decrypting volumes, installation of new disk volumes, volume errors, etc.)
- Rescue information about all encrypted volumes.
Additionally, the administrator can click Recovery Options to prepare rescue file or rescue bootable disk to recover encrypted
disk volume on the selected computer. See the section of this manual entitled
Rescue procedures in Jetico Central Manager
for more details
about how to recover encrypted disk volumes on client computers.
Distributing encryption policies.
The administrator of JCM Console can manage encryption policy on client computers by assigning a policy to the whole group, or to selected computers.
-
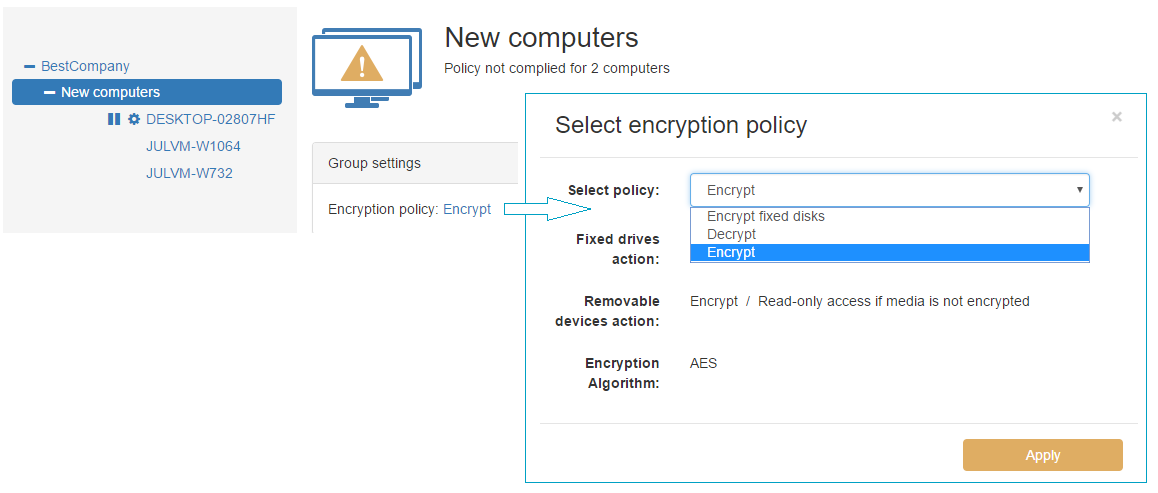
To assign an encryption policy to a group:
- Select the group name in the left panel
- Click on the current encryption policy name
- The Select encryption policy dialog box will appear
- Open the drop-down list of existing policies
- Choose the required policy and click Apply
-
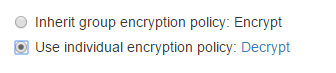
To assign an individual policy to a client computer:
If the assigned policy forces the client software to encrypt fixed disks (in the policy, Fixed drive action = Encrypt), BCVE will ask the user
on the client computer to enter a password to encrypt the volumes. The encryption will start and will be performed in the background.
The process can be stopped, but it will be automatically resumed after a short time or after reboot. As soon as the encryption process starts, the user
will be prompted to enter the password at boot.
NOTE: The automatic encryption may NOT start (or not resume) for the following reasons:
1. The client computer was not rebooted after installation.
2. BCVE main window has been opened on the client computer.
3. The client-server connection has been lost.
The administrator can temporarily suspend client protection (i.e. remove boot-time authentication) In these cases, the volumes will remain encrypted but accessible without a password.
This feature may be required to allow the computer(s) to restart automatically (Windows Updates, backup purposes, etc.). The feature is especially
necessary when managing servers that are required to function around-the-clock.
ATTENTION! The option Suspend protection exposes a security risk. For example, someone can turn off the computer, take it out of the company's
network, turn it on again and gain access to the data. Remember to disable this option as soon as automatic reboot is no longer required.
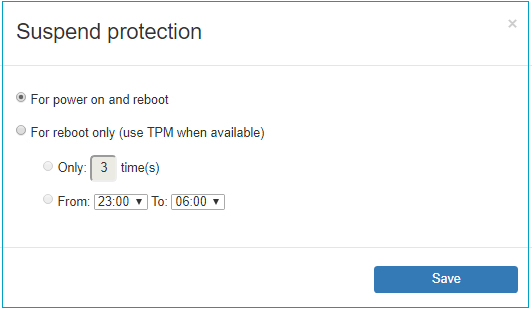
By default, Suspend Protection disables boot-time authentication for all of the following: power on, resuming from hibernation, restart. This can be limited by clicking Options hyperlink that appears next to Suspend Protection checkbox when it is set. The following options are available:
As soon as Administrator enables Suspend Protection, it will be indicated in Activity Log area as follows:
Server: Suspend Protection set for computer 'compluter name'
After that, if the client computer is Online, another message in Activity Log is expected:
Client: Suspend Protection set for computer 'compluter name'
If the client computer is Offline, it will receive the setting and send the log message to the Console after it's connected again. Upon receiving this
confirmation from the client, boot-time authentication is removed.
As soon as Administrator disables Suspend Protection, two records appear in the Activity Log:
Client: Suspend Protection unset for computer 'compluter name'
Server: Suspend Protection unset for computer 'compluter name'
At this point, the boot-time authentication is restored.
Computers with 'Suspend protection' option enabled are marked with the 'pause' icon in the list of computers:
Furthermore, computer status for such computer is set to 'yellow' on the computer page, and the warning is posted: