TPM as the second authentication factor
Previous versions of BestCrypt Volume Encryption (BCVE) create a special TPM index for Unattended Mount at Restart (UMAR) feature storing unencrypted symmetric disk encryption key and leaving NVRAM index unprotected for the bootloader to be able to read the key freely. This feature has a strong security benefit: the key can be securely erased at any time and it is only stored there briefly before erased.
With BestCrypt Volume Encryption version 5 it is now possible to allocate TPM NVRAM index and use it to enhance regular password authorization. Unlike with the UMAR, the TPM index is password protected which allows BCVE to utilize TPM dictionary attack protection capabilities.
Encrypting volumes with the key stored in TPM chip
If TPM device is detected by BCVE, the user can enable the option Use removable device to store the encryption key when running the Encrypt command. The user will be asked to enter a password twice and the TPM device is initialized using the password provided:
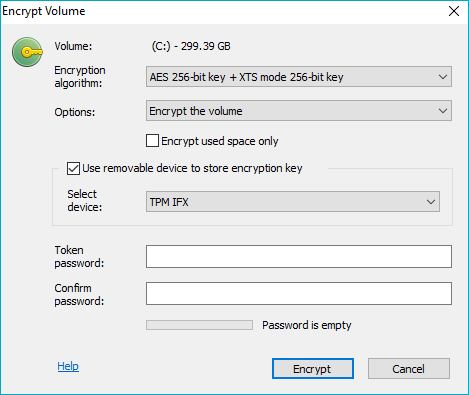
The TPM initialization routine creates a memory region in TPM non-volatile memory which is initialized with random secret and which is password protected. This region is also a subject to TPM lockout policy. For example, 32 consecutive failed authentication attempts result in additional 10 minutes lockout period for each subsequent authentication attempt.
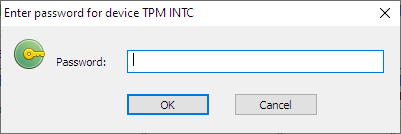
If the TPM device was already initialized earlier, the user will be asked to enter the password that was set when the device was initialized:
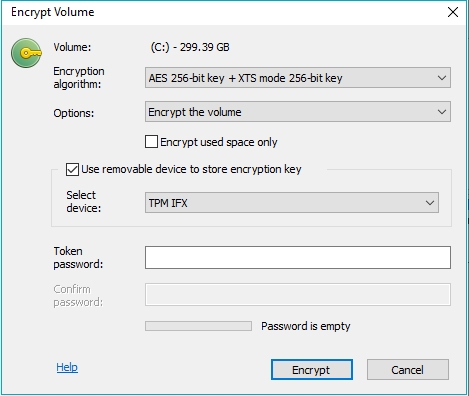
The menu command Volume --> Encryption key --> Delete all keys on external storage removes the BCVE secret TPM index. After that, the device "forgets" the password and should be initialized again.
Hardware compatibility test
If the user is going to encrypt a system volume, the software will need to test whether the TPM device can be accessed and works properly at boot time. The software will suggest the user should reboot the computer to perform the hardware compatibility test and then run the Encrypt command again. If the boot test passed successfully, it will be permitted to store the key for the system volume on the device.
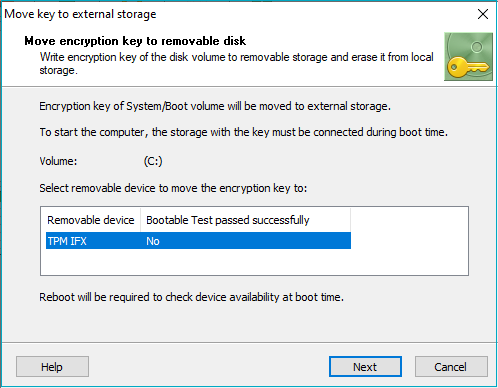
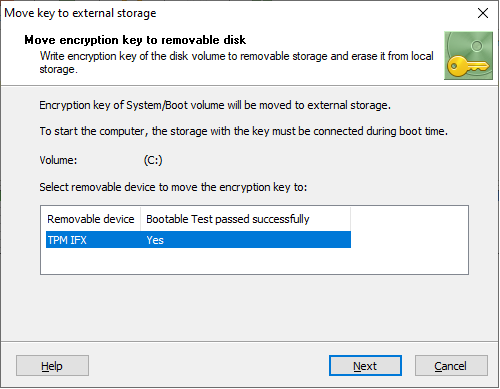
Moving the encryption key from the encrypted volume to TPM device
If the volume was already encrypted earlier, it is possible to move the encryption key to the TPM device to enhance the security level. This functionality is described in Moving Encryption Keys to Remote Storage article.
If the TPM device was not initialized, the user will be asked to enter the password for the encrypted volume and a password to initialize the TPM twice:
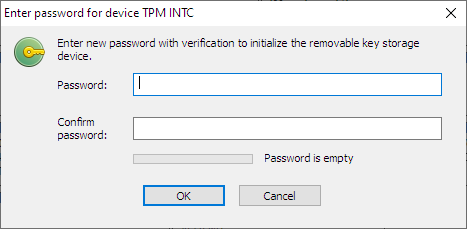
If the TPM device was already initialized, it is required to enter the password for the encrypted volume and then the password for the TPM device:
Limitations of the current implementation
- Only UEFI platform is supported
- Only TPM 2.0, no v. 1.2 support
- All volumes protected by TPM share the same password
- Not possible to make a backup
- Not possible to change volume password while the key is in TPM
- Dictionary attack protection shares parameters with Windows (32 free attempts and then 10 min penalty for each unsuccessful attempt; can also be configured via gpedit.msc)
- The TPM owner can clear the TPM, rendering the keys permanently inaccessible
See also:
Moving Encryption Keys to Remote Storage