Protecting data in process with BestCrypt DataShelter
BestCrypt Volume Encryption encrypts physical disk sectors providing the strongest possible protection when the disk volume is not mounted. When the volume is mounted, all programs and users can access data on the encrypted disk volume exactly as it happens for not encrypted volume.
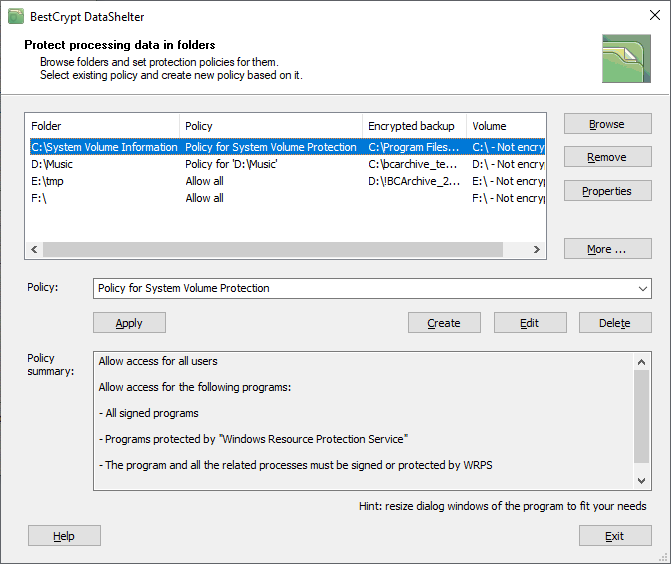
BestCrypt Volume Encryption starting from version 5 provides additional level of protection for folders on the disk volumes with help of the BestCrypt DataShelter utility. BestCrypt DataShelter allows the user to select folders and define a protection policy for them so that only trusted programs and users can access data in the folders. The following picture illustrates main window of BestCrypt DataShelter.
|
|
|
Main window of BestCrypt DataShelter |
The BestCrypt DataShelter can be useful for protecting data in folders for the following scenarios:
- Documents are stolen:
- someone has got remote access to my computer and downloaded the documents
- someone has got physical access to the computer and made a copy of the documents
- Documents are modified:
- the computer is infected by ransomware and the documents are now encrypted so that you cannot access them
- the computer is infected by trojan and someone else reads and/or modifies the documents remotely
- documents are damaged because of the hardware problems
Please note that there are other more traditional approaches to mitigate some of the threats above. Antiviruses analyze running processes and detect the code containing harmful functionality. Firewalls monitor network traffic to prevent unauthorithed access to the computer. The antivirus database with the viruses stamps should be up-to-date, as well as the attack detection triggers in the firewall. BestCrypt DataShelter does not replace the functionality, it concentrates on protecting selected folders by limiting and analyzing processes allowed to access them. The software builds its knowldedge database of what is good and bad from the actual processes and their communications. With this knowledge the user can protect the most valuable files.
Detailed description of BestCrypt DataShelter is available in a separate documentation. Please run command BestCrypt DataShelter documentation from the Help menu of BestCrypt Volume Encryption to read the documentation.