Jetico Central Manager gathers information about using BestCrypt Container Encryption software on client computers. Administrator of Jetico Central Manager becomes informed when some problems arise on the computers with the software. Besides, using BestCrypt Container Encryption becomes safer with Jetico Central Manager support because administrator can provide the user with access to the data inside encrypted containers in emergency cases.
After deployment of BestCrypt Container Encryption software on client computers the Jetico Central Manager Database receives the following information from the programs running on the remote computers:
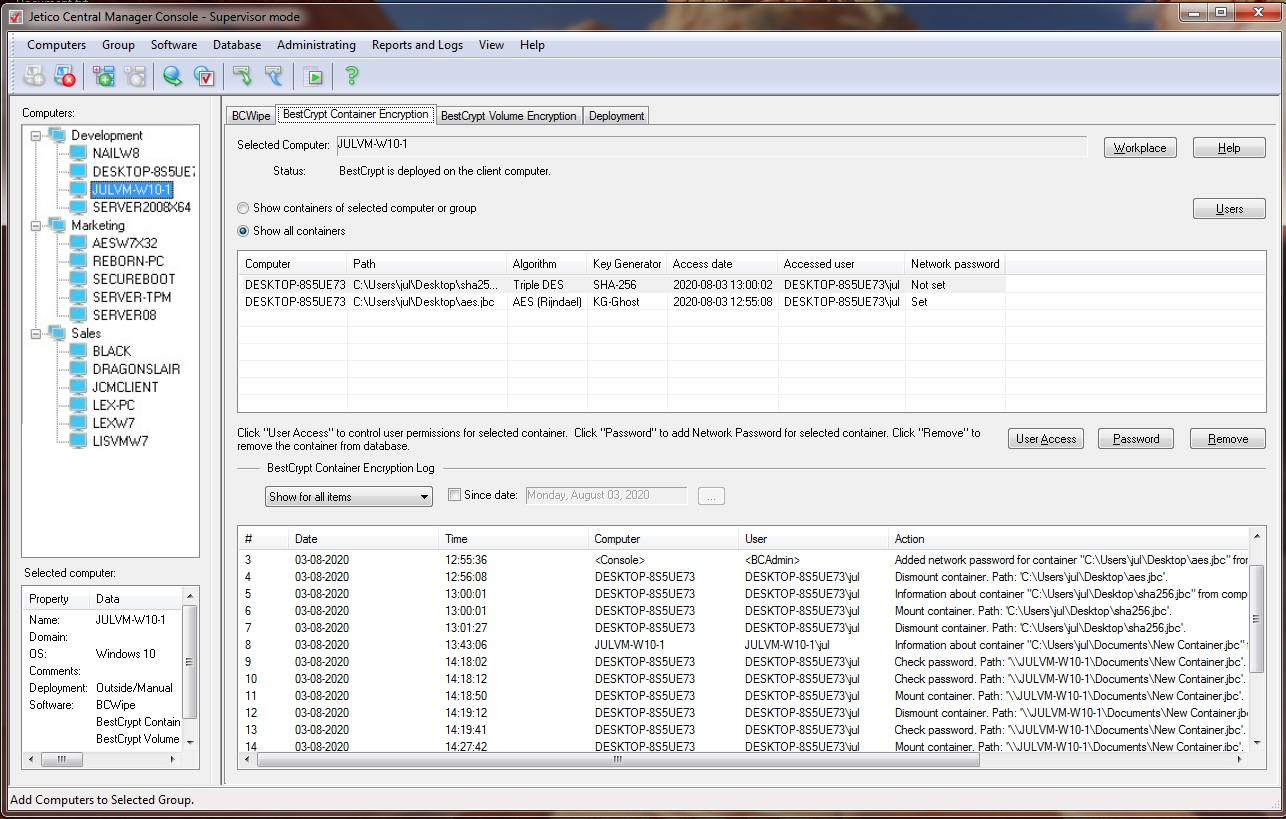
The following picture illustrates the Jetico Central Manager Console when BestCrypt Container Encryption tab is selected:

In BestCrypt Container Encryption tab select radio button Show containers of selected computer/group if you want Jetico Central Manager to list only container files created on computer selected in the left pane of the program. If you select Show all containers option, Jetico Central Manager will show you a list of all container files registered in the Jetico Central Manager Database.
When a user creates or mounts a container, BestCrypt Container Encryption saves encryption key for the container in Jetico Central Manager Database. The database stores the key in encrypted form so that only administrator can manage the key.
If the user forgets password for the container file or an urgent need arises to mount the container file administrator can use the encryption key to get the container mounted. It can be done in the following way:
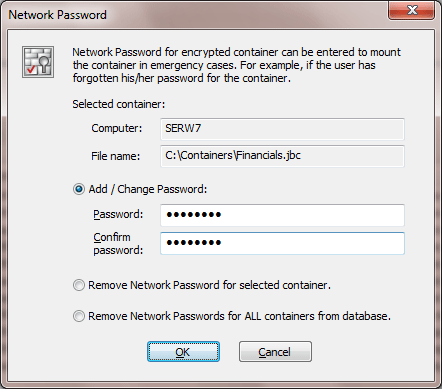
The password administrator enters in the dialog window is called Network password, because when later the user (or administrator) enters this password to mount container file on client computer, BestCrypt Container Encryption software on the computer will send request to Jetico Central Manager Database over network. If correct network password is entered, BestCrypt Container Encryption on client computer will be able to decrypt response from Jetico Central Manager Database and use decrypted key to mount the container file.
If administrator does not need the Network Password for the container anymore, he/she should select the container in BestCrypt Container Encryption tab and click . Then in the Network password dialog window he/she should choose Remove Network Password for selected container option and click .
Since version 2.7 of Jetico Central Manager, the program enables JCM Administrator to control user access to encrypted containers. After the client software is updated and the user logs on for the first time, a message will appear asking the user to create their own password for generating their unique encryption keys (key pair: public and secret keys):
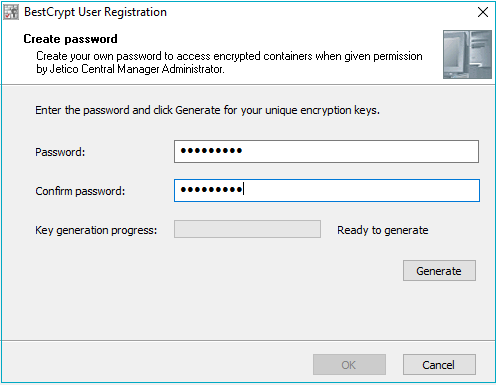
The user's unique keys are then sent encrypted to the JCM Database. After generating and storing the keys, the user becomes 'registered' in the JCM Database.
The list of registered users is displayed in the JCM Console by clicking :
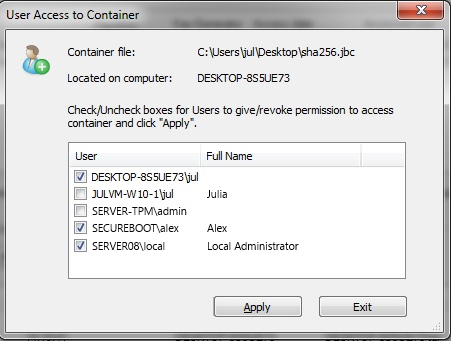
To give permission for registered users to access an encrypted container, JCM Administrator follows these steps in the JCM Console:
After the user gets permission, they will be able to mount the container with the password they created during User Registration. This same user password applies for all containers with permission.
To revoke permission, JCM Administrator unchecks the corresponding box and clicks Apply. If the user had previously mounted this container with the master password, then they will still be able to access the container. In this case, a warning message will appear asking JCM Administrator to change the master password for the container.
Jetico Central Manager removes information about container file when the user deletes the file from BestCrypt Control Panel on his/her computer. There are also other ways to delete the files without running BestCrypt Container Encryption, for example, by formatting drive with the files.
If administrator becomes aware of deleting some container file using not regular way and decides to remove information about the container from database, he/she should select the container in BestCrypt Container Encryption tab of Jetico Central Manager Console and click . Program will warn Administrator about removing all information about the container file from the database and if he/she confirms the operation, the information about the container file will be erased from the database.
JCM administrator can remove any user from the database by clicking the and checking the corresponding box. After that, this user can only mount containers they know the master password for.