BCWipe allows encrypting Windows Swap File. Swap File is the Windows system file that is used for the virtual memory support, and it can store parts of documents, you are working with, in an opened form on hard drive. Even if some powerful encryption program encrypts an original document, Windows can put a whole document or part of it to the Swap file in an opened form. Encryption keys, passwords, and other sensitive information can also be swapped to hard drive. Even if you use all of the security advantages of the latest Windows versions, simple investigating of the Swap file in DOS mode may allow extracting a lot of information from the file.
Note: The same window appears when you click on Wiping Options property page in the dialog window associated with Delete With Wiping or Wipe free space right-click menu commands.
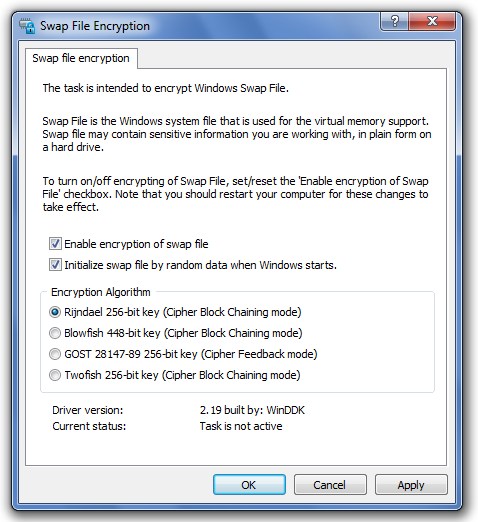
To turn on/off encryption of the swap file, set/reset the Enable encryption of swap file checkbox. Note that BCWipe will start (or stop) encrypting the Swap file only after reboot. If the computer is not restarted after enabling the utility, Current status is reported as Not active, and vice versa - if you disable the utility and have not restarted computer, Current status is reported as still Active.
Swap File Encryption utility (called also CryptoSwap) allows choosing one of the following encryption algorithms - Rijndael, Blowfish, GOST 28147-89 or Twofish.
Encryption key is generated from random statistics, like nanoseconds timing intervals, when Windows boots up, and new key is generated every time when computer is rebooted. CryptoSwap utility does not store the key somewhere on disk, it “forgets” the key after rebooting the computer.
Note: CryptoSwap will start (or stop) encrypting the Swap file only after reboot.
Swap File Encryption utility (CryptoSwap) loads low-level driver when Windows is started and before the operating system runs its virtual memory support mechanism and initializes the Swap File.
At the time of initialization the driver generates random encryption key, which is unique for the current Windows session. Encryption key is generated from random statistics, like nanoseconds timing intervals, and new key is generated every time you reboot computer. The CryptoSwap utility does not store the key somewhere on disk, it “forgets” the key when you reboot or shutdown computer.
The CryptoSwap driver intercepts all filesystem operations, like open/close, read/write file and others, detects requests to the system Swap File and encrypts data buffers when Windows writes something to Swap File. Similarly, when Windows reads data from Swap File, CryptoSwap decrypts the data. Hence, activity of the CryptoSwap utility is transparent for the operating system and for running applications.
When you reserve, for example, 5 Mbytes for an usual new file, the operating system clears the reserved 5 Mbytes of disk space with zeros. It is not so for the Swap File. When Windows boots up, it reserves disk space for the Swap File without re-writing the reserved disk space.
As a result, the following effect may occur. CryptoSwap starts to encrypt all the read/write operations to the Swap File, but activity on computer is not too high, and there is no need to use the Swap File. Hence, encrypted information won't be written to the disk space, reserved for the Swap File.
Now we boot to DOS and notice that only a small part of the Swap File (pagefile.sys) has been encrypted,
all the other space in the file is just garbage, stored earlier on the disk. Since the ‘garbage’ can also
contain some sensitive information, it is recommended to check
Initialize swap file by random data when Windows starts checkbox.
Another solution is running Wipe Free Space command with Swap File Wiping option at least once, when you turn on encrypting Swap File for the first time. After that you do not have to use Swap File Wiping option at all, because contents of the Swap File will be encrypted.