Technical Details about Managing Keys on Yubikeys
YubiKey is an USB cryptographic device which pretends to be a HID keyboard. There is the list of prerequisites for using a Yubikey with BCVE
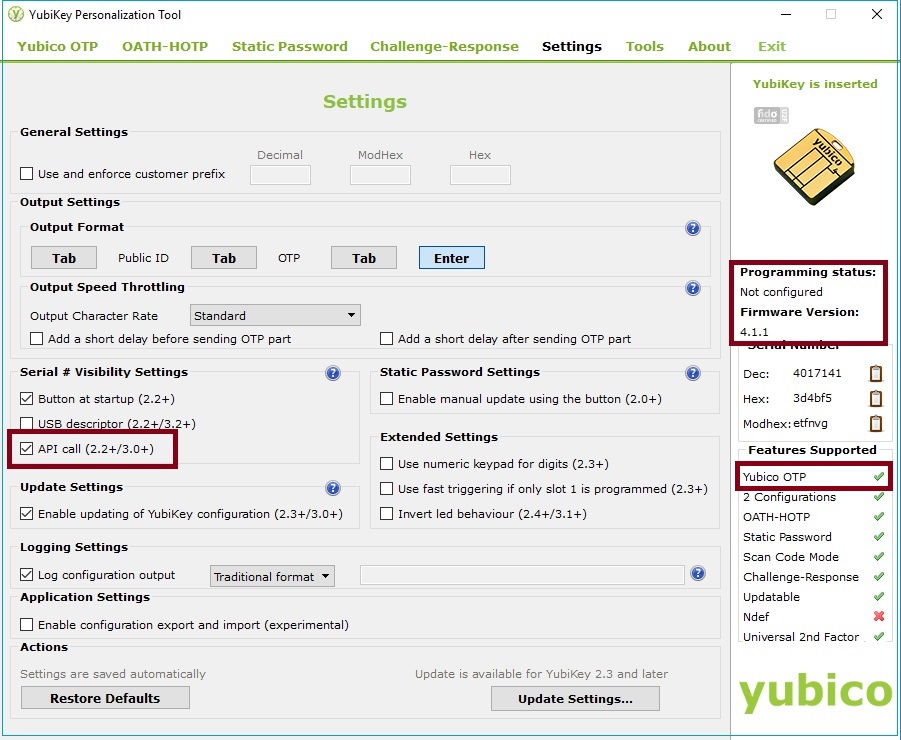
(use Yubikey Personalization Tool for configuration):
- All slots must be unconfigured (usually, the device ships with at least one slot configured).
- OTP mode should be enabled (enabled by default but may be manually disabled with command-line tool ykpersonalize);
- "Configuration protection" (aka PIN) is not supported and must be disabled; (open Challenge-Response tab to view the setting)
- Firmware version: 3.0-3.5, 4.0-4.4, 5.X (some of the 2.3+ may also work but has not been tested);
- "API Serial visible / API call" must be enabled;
To start using your YubiKey device with BCVE the device must be initialized (or provisioned).
The initialization will be performed by BCVE at the time when you move the key to a removable key storage. During initialization the first two slots will be configured to operate in Challenge-Response mode.
BCVE uses YubiKey in Challenge-Response mode in order to generate cryptographic keys without exposing sensitive data over insecure transports and storages.
Each Challenge-Response slot is able to carry up to 20 bytes of non recoverable data. BCVE claims two slots for its own needs. Since some of the YubiKeys (older versions) has only one slot thus it is not possible to use such devices with BCVE.
Once device is initialized it stores a second factor worth of a secret, randomly generated 20 bytes.
The first YubiKey slot is used to identify YubiKey as claimed by BCVE. This prevents situation when the user accidentally erases sensitive data on the device by using it on the second PC. The second slot is used by BCVE in order to generate a key for a symmetric block cipher.
Any two volumes which share the same YubiKey also share a second factor.
The user can encrypt any number of drives on a single PC under a single user but with other PC or user the device will refuse to work.
Removable drives are only possible to decrypt with YubiKey on the same PC where they were encrypted.
In order to move the key from any volume to a YubiKey token BCVE must know beforehand the exact 20 bytes of 2nd factor for that particular device. In order to do that BCVE enforces a limitation that all volumes encrypted with given token must have the same password. This limitation might be loosen in the future.
BCVE doesn't allow to share YubiKey between different PC or users.
Any volume encrypted with YubiKey stores volume key and a copy of second factor. Both of them are encrypted using AES algorithm with a generated key.
The key for this symmetric cipher is produced based on the volume password, salt, YubiKey's response and a nonce.
BCVE uses 32-bit continuously growing sequence number as a nonce.
The secret should also be stored on the volume in an encrypted form in order for BCVE to be able to encrypt the volume key in secure manner every time the user mounted a volume.
After the volume key is decrypted given the procedure above BCVE keeps the secret tightly shut on the device.
Upon every successful mount attempt BCVE encrypts stored volume key and a secret with a newly generated nonce.
BCVE stores both volume key and a second factor on the volume in an encrypted form.
To use YubiKey further with any other user or PC the device must be cleared. The user can delete all configuration slots manually using YubiKey Personalization Tool or by using BCVE command Volume -> Encryption Key -> Delete all keys from token
BestCrypt Volume Encryption maintains a detailed log file with low-level events (appdata\Jetico\Tokens.log)
Refer to the Yubico website for more details.
See also:
Encrypting and Decrypting Volumes