Customized Parameters for Scrypt Algorithm
When you enter password to get access to the data on the encrypted disk volume, BestCrypt Volume Encryption runs algorithm called Scrypt to derive encryption key from the password. The chapter Security Characteristics explains:
Scrypt requires intensive computational resources to derive a key from a password and it allows customizing its internal variables to make the computational efforts even harder. As a result, attacking passwords becomes a substantially more difficult task because of the long time and intense processing power required to test every password.
A detailed Scrypt algorithm specification is available in the RFC 7914 document. What can be customized in the algorithm are the parameters N, P and R. In short, the parameters can be explained as the following:
- N - iterations count (affects memory and CPU usage). Default settings in the software: 32768
- P - parallelism factor (threads to run in parallel - affects the memory, CPU usage). Usually 1, and it is a default setting in the software
- R - block size (affects memory and CPU usage). Default settings in the software: 16
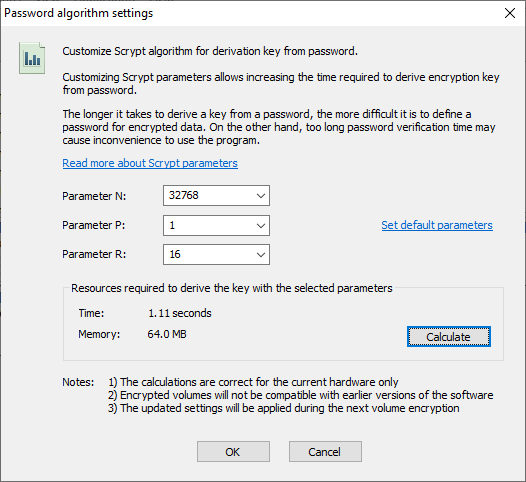
If you wish to make attacking your passwords harder and increase amount of calculations and time required to derive the encryption key from the password, you can customize the Scrypt parameters. To do that run command Algorithm settings from the Password menu. The following window should appear.
|
|
|
Scrypt algorithm parameters |
The Password algorithm settings window allows the user to do the following:
- Change Scrypt parameters N, P and R. Please note that it is possible to enter extremely high parameters so that the calculating key from password will require hours or days
- Set default Scrypt parameters by clicking corresponding link control. It can be required when you are going to encrypt some disk volume (usually removable) that will be necessary to mount with the earlier versions of the software
- Run test procedure of deriving key from password to estimate the time necessary for the procedure on your computer hardware. It is recommended to click the Calculate button after changing the Scrypt parameters to verify that the algorithm is able to perform its calculations for a reasonable time
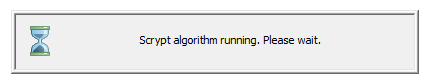
After increasing the Scrypt parameters, it will be possible that the software will need, for example, dozen seconds to verify the password you enter to mount encrypted disk volume. BestCrypt Volume Encryption displays the following window at that time:
|
|
|
Scrypt algorithm reports about running calculations |
The software can show the window several times, even before prompting the user to enter the password.
NOTES:
1. When you change Scrypt parameters, the new settings will take effect for the disk volumes you are going to encrypt. Volumes that are already encrypted will not have the Scrypt parameters changed.
2. If you change Scrypt parameters, you will not be able to mount encrypted disk volumes with previous versions of the software. Please use the default Scrypt parameters if, for example, you plan to encrypt removable devices and then mount them on computers with earlier versions of the software.
3. The encryption key derived from the password with the Scrypt algorithm is not used directly to decrypt data on the encrypted disk volume. The software uses the derived key to decrypt another Data Key to decrypt the data. So when you change the password, the derived key is changed and the Data Key is re-encrypted with the new derived key. Such a procedure is more secure and allows changing password quickly without re-encrypting entire disk volume.
See also: