BestCrypt Volume Encryption utilizes Trusted Platform Module (TPM) hardware available on many motherboards for the purpose of unattended reboot of computers with encrypted boot/system disk volume.
The feature is necessary to manage servers that are required to function around the clock. If such a server has boot/system volume encrypted, every reboot of the server requires manual entry of a password at boot time. This poses a problem when the server must be rebooted automatically: for example, when the installation of operating system updates requires a reboot of the server. System administrators typically configure automatic reboots to happen at times when minimum activity is running on the server (in the middle of the night for example). If a system/boot disk of the server is encrypted, during reboot the server will display the password prompt at boot time. The operating system will not boot until the administrator enters password when he/she appears in front of the server console next morning. In the mean time, the server will still be waiting to boot.
The option to reboot the computer without requiring to enter password at boot time exposes a security risk. For example, someone can turn off the computer, take it out of the company, turn it on again and get its boot/system volume mounted. If Mount at boot time option is set for a non-system data volume, it will also be mounted for access automatically.
To minimize the security risk as much as possible, BestCrypt Volume Encryption does the following:
To set the option, run the command ->Unattended mount at restart. The following dialog window will appear.
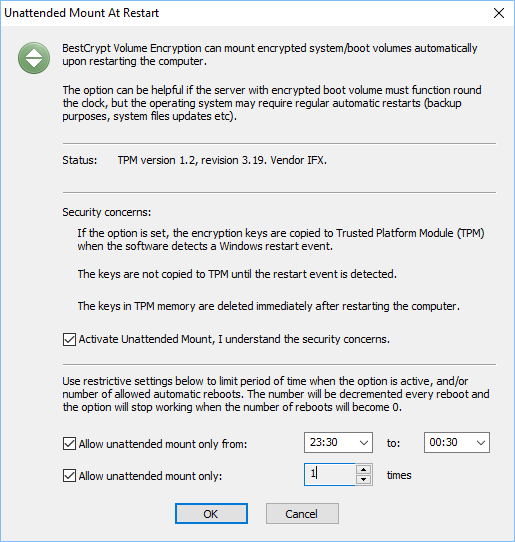
The window explains the security concerns that the user should understand and requires marking corresponding checkbox to activate the option.
The dialog window also explains how the user may set restrictive settings for the option to make its use more secure: limit the time period when the option is active and limit number of times the computer can be reboot in unattended mode.
The Unattended Mount At Restart option can be activated only on computers with Trusted Platform Module (TPM) hardware.
Only a user with administrative privileges can set this option or change its settings.
To be able to work with the TPM hardware, the software must enter TPM Owner Password. It is required once only, when the user runs the "Unattended mount at restart" command for the first time.
In versions of Windows before Windows 10 the user configured the Password with some utility provided by the TPM hardware vendor. Hence, the user is aware of the Password and can enter it when the software asks about the password.
The way of configuring TPM software by the user called "Legacy" in Windows 10, although it is still possible to do that. In this case Windows 10 will refuse using the TPM hardware, for example, to encrypt disk with its BitLocker utility.
There are two other ways of utilizing TPM that Windows 10 prefers:
The way of generating TPM Owner Password can be configured in the following Windows 10 Registry key: "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\TPM" where value "OSManagedAuthLevel" can be set to one of the follwing:
Read more about the TPM settings in Windows 10 in Microsoft Change the TPM owner password article.
To be able to use BestCrypt Volume Encryption command "Unattended mount at restart" in Windows 10, you should configure Windows 10 so that it would generate random TPM Owner password and remember it.
NOTE: When you change the way of managing TPM Owner Password in Windows 10, the operating system erases its keys stored in TPM hardware. So if you have some disk encrypted with Windows BitLocker, please decrypt it before changing the TPM settings.
Do the following to configure Windows 10 TPM settings:
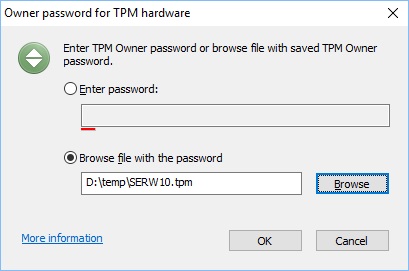
Select option Browse file with the password and enter path to the file where you have saved the TPM Password.
The software will accept the password and configure the TPM hardware for further use of the option. There will be no need anymore to enter TPM Owner Password again in the software. The user can even return the default Windows option back to erase the password and even run Clear TPM command in Windows tpm.msc utility. BestCrypt Volume Encryption will be able to work with TPM after a single successful action to configure TPM for its own purposes.