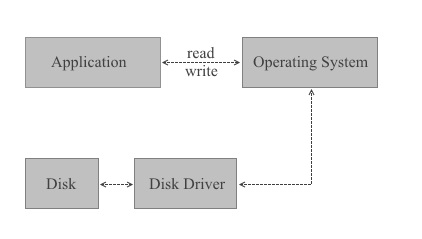
When BestCrypt is not installed, all read/write operations required by application programs (a text processor for example) are performed by the operating system (Windows 8.1, for example) with the help of a disk driver (usually a part of operating system):
When BestCrypt is installed, its driver monitors all read/write requests and performs encryption/decryption of the transferring data on the fly.
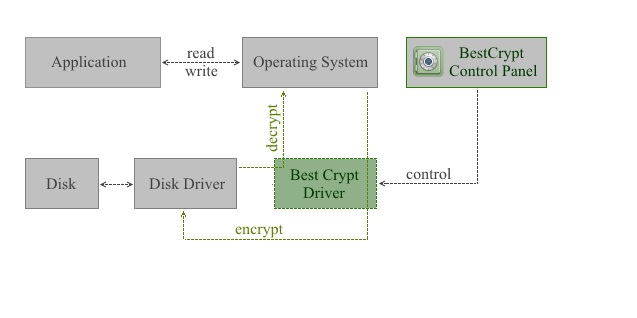
Not all I/O requests are processed by the BestCrypt driver. Instead, the driver creates and supports its own virtual drives. Only I/O operations for these virtual drives are processed with the BestCrypt driver. These virtual drives are visible as typical disks with corresponding drive letters (for example, D:, K:, Z:, i.e. with any drive letter that is not used by other system devices).
Any free drive letter in the system may be used to mount and to open an encrypted file-container for access. When the virtual disk is opened, you can read and write data as if it were a conventional hard disk.
The data stored on a BestCrypt virtual drive is stored in the container file. Of course, the size of a virtual drive is equal to size of the linked container. A container is a file, so it is possible to backup a container and then to restore it, if there is a mishap.
The BestCrypt system allows users to choose cryptography algorithm and encryption mode for storing sensitive data. Different encryption algorithms can be used in different containers. BestCrypt can re-encrypt the data if the user wants to change the encryption algorithm.
Easy-to-use BestCrypt software has been developed to simplify all control procedures as well as to satisfy all security requirements. For this reason the BestCrypt system is the ideal product for a wide range of users - from the government services and commercial agencies, to the people who keep private letters on their home computers, to those who travel on business trips and use their notebooks for storage.