This chapter gives a quick overview of all the major components of the BestCrypt data encryption system and provides an introduction to a few basic concepts that are used throughout the rest of this guide.
To achieve its goals in providing the best in data protection, BestCrypt utilizes four major components:
In the following section, we will take a closer look at each of these components.
Control Panel is the main BestCrypt command and control application. Virtually any function supported by BestCrypt is available through its functions and dialogs, which include:
Control Panel provides a wide variety of functions, all of which are fully explained in the BestCrypt Control Panel section.
To launch the Control Panel, find BestCrypt in your "/Applications" folder and double click.
Resident Agent is a specific BestCrypt component that runs in the background when your computer is working. You can locate its taskbar item to access its functions:
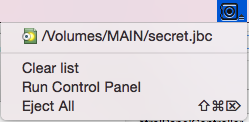
When a computer boots up, Resident Agent's first task is to check what containers you specified to be mounted upon your logging on and then to display a mounting dialog for each of them. You can also see its task bar item menu on the screenshot above. This menu displays a list of known and currently mounted containers. You can use this menu to quickly mount and eject containers by simply clicking on the associated item. It also allows you to quickly eject all currently mounted containers by either clicking Eject All or using a system-wide hotkey.
BestCrypt provides its Finder Service to integrate common container functions directly into your workflow:
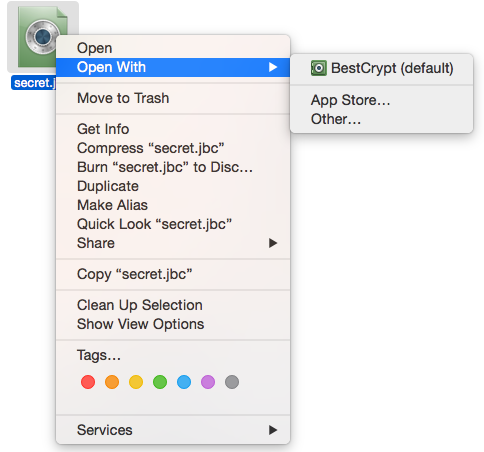
Double-clicking on any BestCrypt container file from a Finder window will mount that container or open its content if it is already mounted. The item in the Finder context menu called Open With > BestCrypt (default) has the same functionality.
The main unit all BestCrypt components operate on is called the BestCrypt Container File. True to its name, it represents a file on your system with a specific default .jbc extension and the icon shown below:

This file contains all encrypted data stored on the virtual disk contained within it. Each container file stores at least one main virtual disk and can also store a number of additional hidden disks. You can imagine a container file as a collection of encrypted disk images with all data required to verify passwords and perform all other operations.
A BestCrypt container file has a well-known format that exists in a variety of versions and is described in more detail in Appendix B, BestCrypt Container File Structure. Of course, you don't need to know all the details of container file structure to fully and easily use BestCrypt. For purposes of this general introduction, it is sufficient to simply say that container file consists of two main parts:
BestCrypt provides a number of operations that deal specifically with a container file's service header, including backing up key data and header encryption. These operations are explained in more details in other sections of this guide.
Some versions of the container file format are declared deprecated and can't support newer functionality. Of course, by default, only the latest format is used when creating new containers.
For help with creating new container files, refer to Creating a New Container.
Encrypted data stored inside a container file can be mounted with the correct password and accessed from a virtual encrypted disk. This disk emulates an ordinary removable device (like a thumb drive) with the exception that all files written to it will be stored encrypted in the container file this disk was mounted from. When reading existing files from the disk, all data will be read from its container file and decrypted.
Every single application -- be it Finder, a text editor or even Terminal -- will work with virtual encrypted disks as usual. All encryption and decryption is performed transparently for every single bit of data located on each encrypted disk. This allows BestCrypt to easily and seamlessly integrate into your day-to-day workflow, while you simultaneously get automatic and transparent data protection.
The process of decoding a virtual encrypted disk from container file is called mounting. There are several ways to mount a BestCrypt container:
No matter how you've chosen to mount your container, you will be greeted with the Container Mount Dialog:
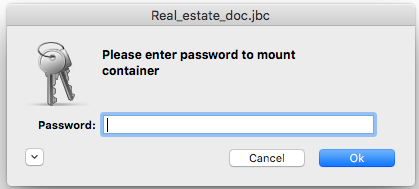
The simple view contains:
The advanced view, which you can view by clicking the small button in the bottom-left corner of the dialog, contains the following checkbox options:
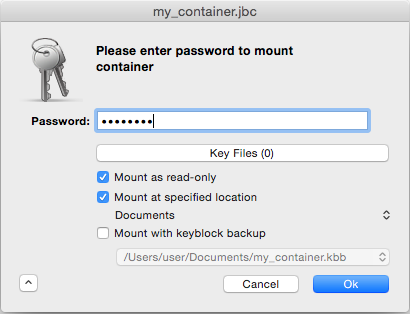
After the container password and selecting all desired options, click to verify the password and mount the container.
On a Mac, all your mounted disks, whether real or virtual, are attached to one big file-system hierarchy. New disks can be attached to any folder anywhere in this hierarchy as long as you are allowed to access the folder. On a Mac, there is a default folder where new disks are mounted, called /Volumes. For each new disk, a new folder is automatically created there and all the disk's contents become accessible from that folder. However, nothing stops you from mounting your new disk at any other custom location. In this case, the contents of the new disk will be accessible from this custom location and any previous contents of that location will be "hidden under" the disk contents. Once you eject the disk, previous folder contents will become visible again.
You can use this behavior to your advantage to intentionally hide previous folder contents under the contents of the BestCrypt container. One typical application of this trick is to mount a BestCrypt container right on the folder where this very container file is located. This way, the actual container file will be hidden as long as its virtual encrypted disk is mounted.
You can eject encrypted disks the same way you would eject an ordinary flash drive: using the eject button in Finder's disk panel or the DiskUtility application. BestCrypt, however, also provides additional ways to eject mounted containers that complement standard ways described previously and add additional functionality to this process: