A lot of people around the world have their secret (private) and public keys. They make their public keys opened for everyone and keep corresponding private keys in a secure place. Public key can be used by anyone to encrypt data, but only an owner of corresponding private key can decrypt the data.
Using BestCrypt v8+, you can create containers and archives encrypted with public keys. If you decide to send an encrypted information to your friend John, you should create BestCrypt archive, and encrypt it with John's public key (see Help documentation for Enhanced Hidden Containers technology utility). As for containers encrypted with public key, they are used in a different way.
Imagine that several users need to access a container stored on a shared network drive. Each user is given a public/secret key pair, generated by BestCrypt Key Manager or other utility. Administrator creates the container with his/her password or public key and then adds public keys of all other users with Add Password command. Thus, every user can access the container using his/her secret key, and there is no need to expose password of every user to administrator.
To create a new container with public key encryption, open New Container dialog, fill in all the fields in the dialog window and click .
When Enter password dialog appears, click and choose Public Key Encryption in Key Block Type edit box. The following dialog window will appear:
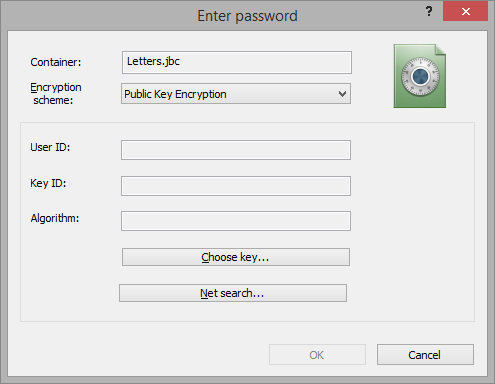
Select public key of the user who will be able to mount the container. There are two ways of choosing the key - first, get the public key from your Local Key Database, second - find the public key in some Public Key Database available in the Internet.
To encrypt the container with a public key stored in your Local Key Database, please click button. List of public keys stored in your Local Key Database will appear:
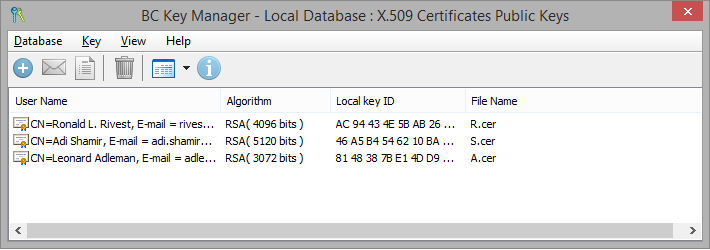
To choose a key, please double-click on the key or click right mouse button and select Get the key command. Key Database window will be closed and you will return to the Enter password dialog. All the information about the chosen key now appears in User ID, Key ID and Algorithm areas:
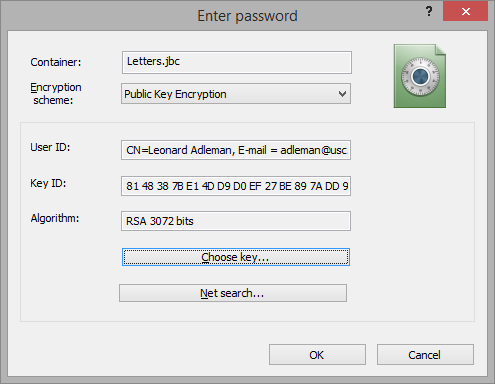
Press button to finish the process of creating container.
If you want to find public key of some person in the Internet, click . BestCrypt will display a list of Public Key Servers in the Internet. You can choose some Server, find public key of the person and continue creating new container that will be encrypted by the person's key.
Note that after creating the container only the person who knows secret key and knows password for it will be able to mount the container file.