| |
|
|
|
|
|
Using BestCrypt |
This chapter briefly describes common BestCrypt practices. All data protected by BestCrypt are stored in conatiners
or special encrypted files. The first step in using Best Crypt is container
creation. Note that BestCrypt for Linux containers are compatible with BestCrypt
v6.0+ ones. If you already have BestCrypt v6.0+ containers you can jump to Step
3 now. 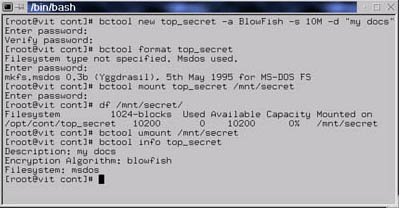
Detailed instructions on using BestCrypt will be given in later sections; here we provide simple examples only. Note that most commands require container password, although it will not be reflected in this very short description. So let's begin ... you can create a container with following command (Step 1):
[foo@bar ]$ bctool new secret_data -a GOST -s 10M
Details...
Next, you should create filesystem on container (in other terms, format it). To do this, issue (Step 2):
[foo@bar ]$ bctool format secret_data -t msdos
Details...
In order to access data stored you should mount your container. Mounting is performed by following command (Step 3):
[foo@bar ]$ bctool mount secret_data /mnt/secret
Details...
Now you can use your container. Encryption performed by BestCrypt is transparent;
you can't see any differences between ordinary and BestCrypt protected files.
Your system does not distinct BestCrypt protected and ordinary files too. So
you can run any system utilities on BestCrypt protected files.
When you decide to finish, you should hide and lock your sensitive data. To do
this you need only unmount the appropriate container (Step 4):
[foo@bar ]$ bctool umount /mnt/secret
Details...
The work cycle is complete. See also full categorized command list.
| |
|
|
|
|
|