| |
|
|
|
|
|
BestCrypt Basics |
BestCrypt software has been developed for ease of use while still providing strong security for your data. BestCrypt is the ideal product for a wide range of users - from the government services and corporations to the home users. BestCrypt is ideal for frequent travellers who wish to take confidential work files or accounting records with them - no longer should there be concern about the loss of theft of sensitive information.
BestCrypt makes use of containers - secure data storage to protect your data. Containers are always kept encrypted by proven industrial strength ciphers; access to container data is controlled by password. Container is a regular file, so it is possible to backup a container and then restore it, if there was a mishap.
Container file can be mounted to virtual drive created and controlled by BestCrypt software. This means that all I/O operations for virtual drives are processed by the BestCrypt driver. Of course, the size of a virtual drive is equal to size of the linked container. The virtual drive can only be accessed if correct password supplied. Without the correct password all data on the virtual drive are inaccessible.
| Note: |
If you forget your password you will NOT be able to access your encrypted data. BestCrypt encryption does not allow you to "recover" information without knowing the password and the software contains no "back door". You lose your password you lose your data. |
Once the correct password has been supplied and container is mounted as a new virtual drive and it can be used in the same manner as conventional data storage, e.g. hard disk or floppy. The virtual drive managed by BestCrypt looks like an ordinary disk and you can store your files on it. Every read operation on the virtual drive causes decryption of the data and every write operation causes encryption of data. This approach is called transparent encryption - your data is always stored in a safe, encrypted form and appears in its natural form in any of your desktop applications.
|
|
|
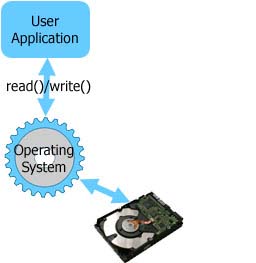
Before BestCrypt installation Application program (e.g. text processor) performs read/write operations. All read/write requests are served by disk driver - usually a part of operating system |
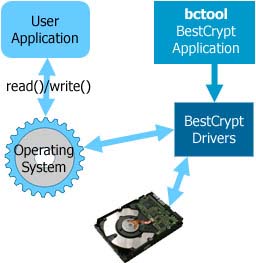
After BestCrypt installation BestCrypt monitors all read/write requests and performs encryption/decryption on the fly. |
The BestCrypt modular encryption architecture allows the use of different encryption algorithms simultaneously: one container could be encrypted with the GOST standard while another is encrypted with Blowfish or Rijndael. Moreover, BestCrypt will re-encrypt the data if the user would like to change the encryption algorithm.
| |
|
|
|
|
|